Stop email attacks, protect sensitive data, and simplify your security operations
Material Security provides unified protection for Google Workspace and Microsoft 365, combining threat detection and response across email, files, and accounts. With a single platform, you get stronger defenses, clearer visibility, and simpler operations—all without the complexity of legacy tools.
With Material Security you can:
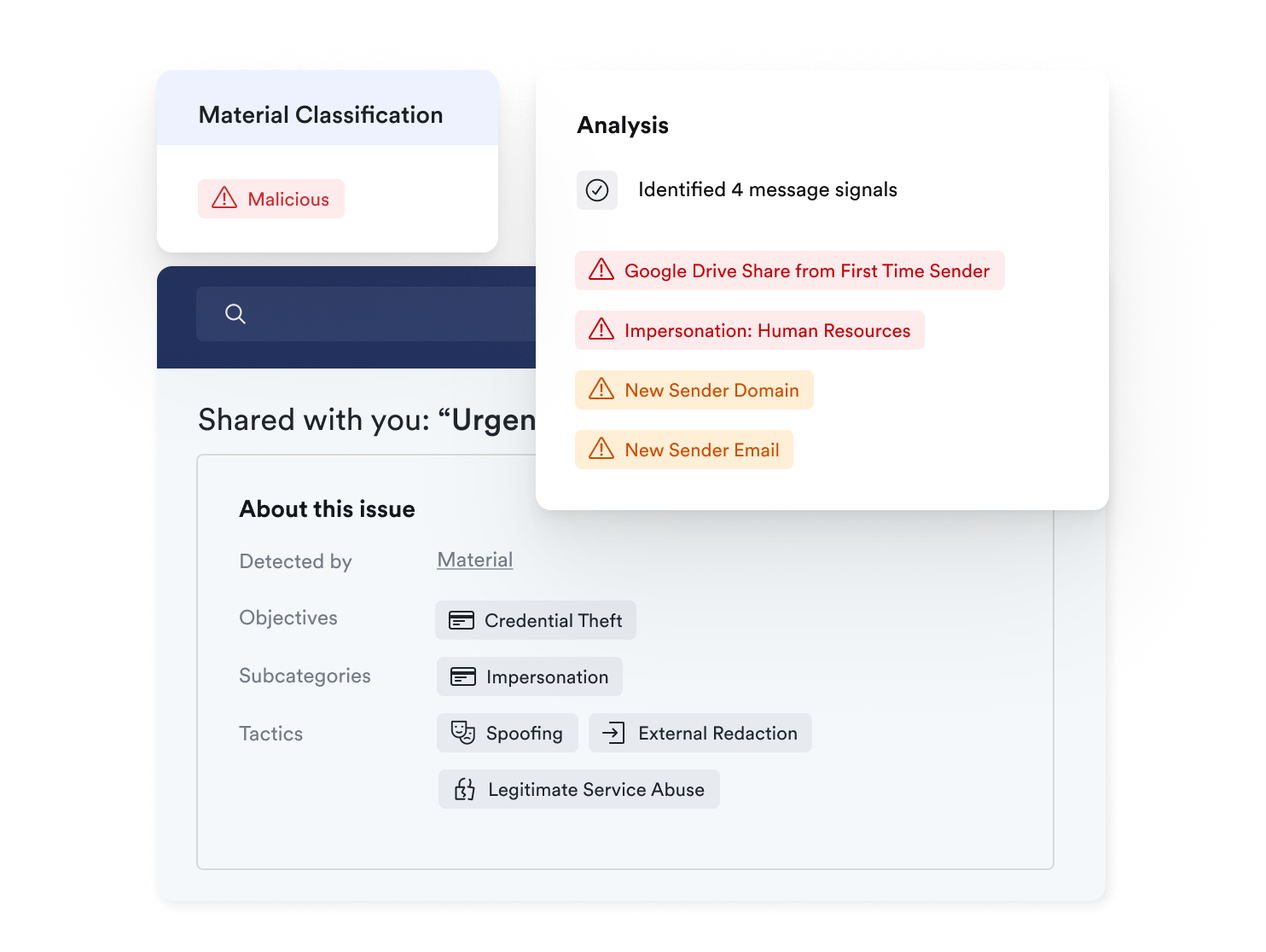
1. Detect and remediate advanced threats like phishing, BEC, and account takeovers that slip past traditional email gateways or Microsoft/Google-native defenses.
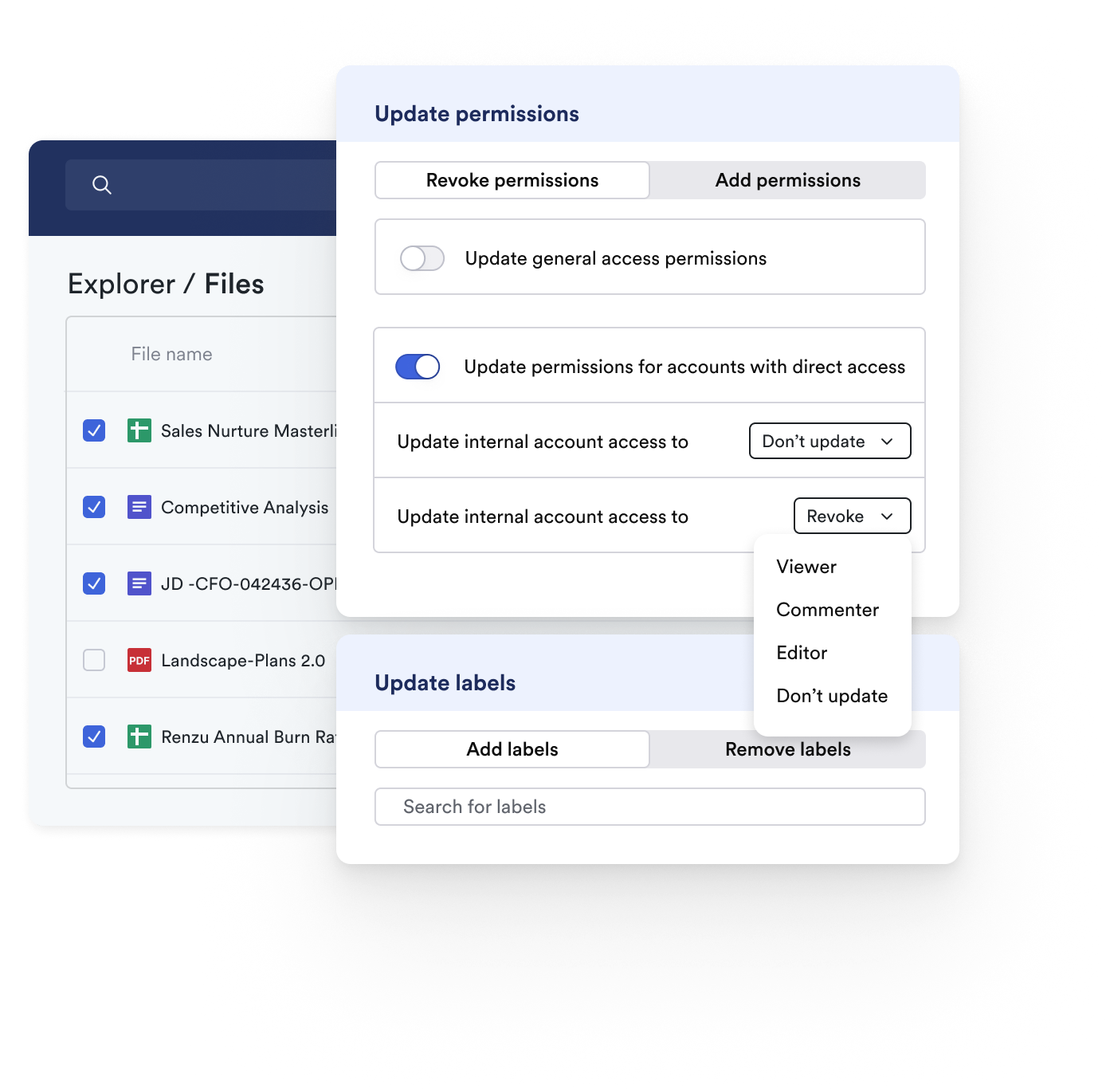
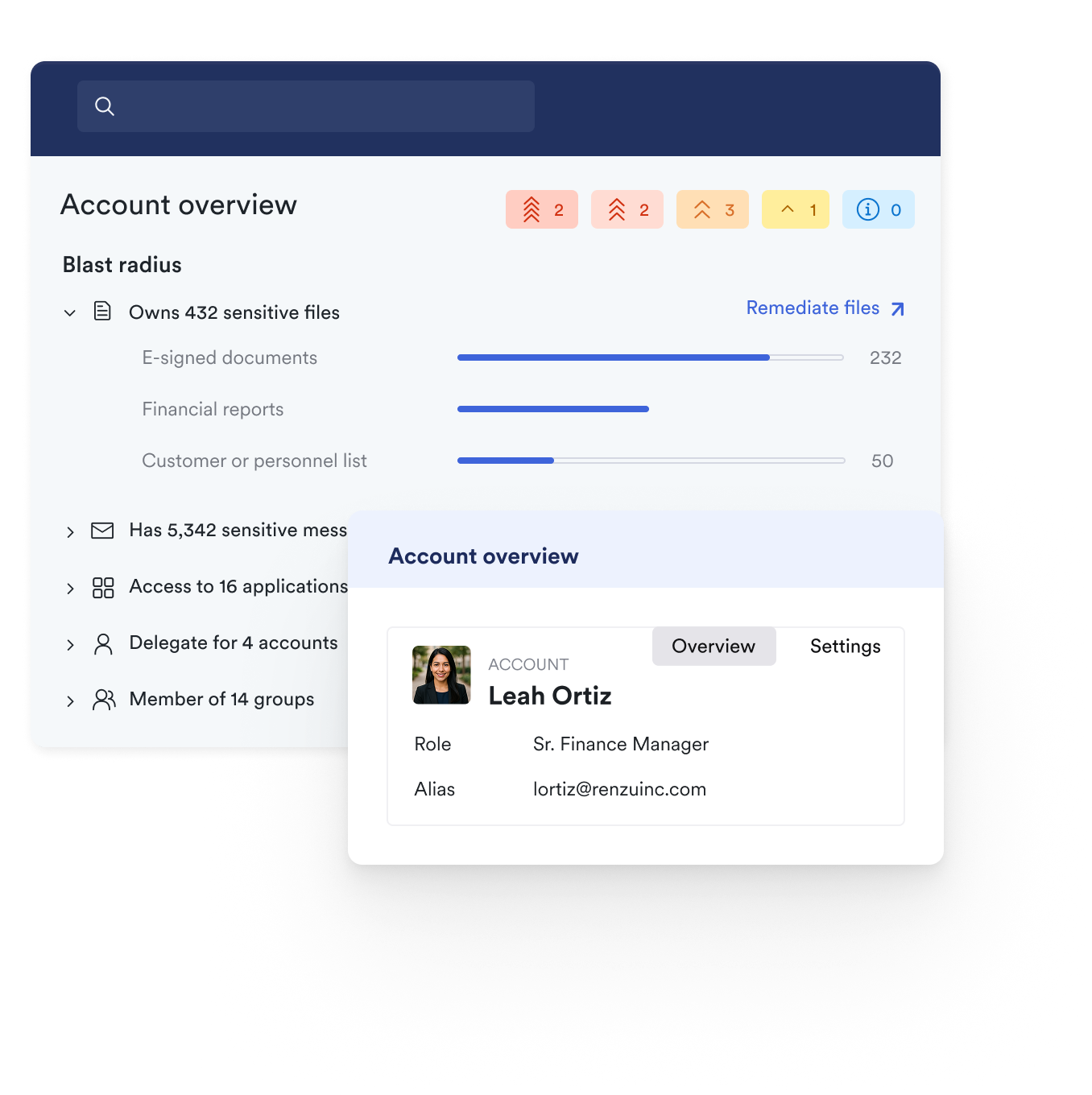
2. Gain complete visibility into where sensitive data lives and how it’s being shared across inboxes and Google Drive.
3. Eliminate quarantines, noisy alerts, and repetitive manual tasks while providing your team with real-time insights into account risk, file exposure, and attack activity.
-svg.svg)

%20(1)-svg.svg)
.svg)
-svg.svg)


-svg%20(1).svg)





%20(2).avif)

.svg)





See why security and IT professionals rave about Material Security
.png)

"I feel a lot more confident about our defenses against phishing and confidential data leakage. Material helps me sleep better at night."
.jpeg)
"It used to take me 20-30 mins to investigate a single phishing email. Today I received 5 or 6 phishing emails and spent only 2-5 minutes in Material."
How Material secures your email, inside and out

Seamless, Agentless Deployment
Get started in hours—not weeks. Material connects directly via API to Google Workspace and Microsoft 365, with no endpoint agents or complex re-routing.

One Platform, Complete Protection
Go beyond just scanning inboxes. Material unifies email, files, and accounts into one security platform—closing gaps that point solutions leave behind.

Automated, Always-On Remediation
From phishing emails to risky file shares to suspicious account activity, Material detects, remediates, and responds automatically, adapting to your risk tolerance.

Total Visibility Without the Noise
Search across every email, file, and account with precision. Material groups related threats into clear, actionable cases, eliminating noise and false positives.

Clear, Actionable Insights
Material delivers deep visibility into your cloud workspace, showing exactly where sensitive data lives, who has access, and the potential blast radius of any compromised account.

Integrates With Your Existing Stack
Material extends and enhances your existing tools by connecting seamlessly with your SIEM and SOAR platforms.