Critical protections for your critical material
Don't waste your email security budget on a point solution.
Stop attacks, secure sensitive data, and strengthen security posture across Google Workspace and Microsoft 365.
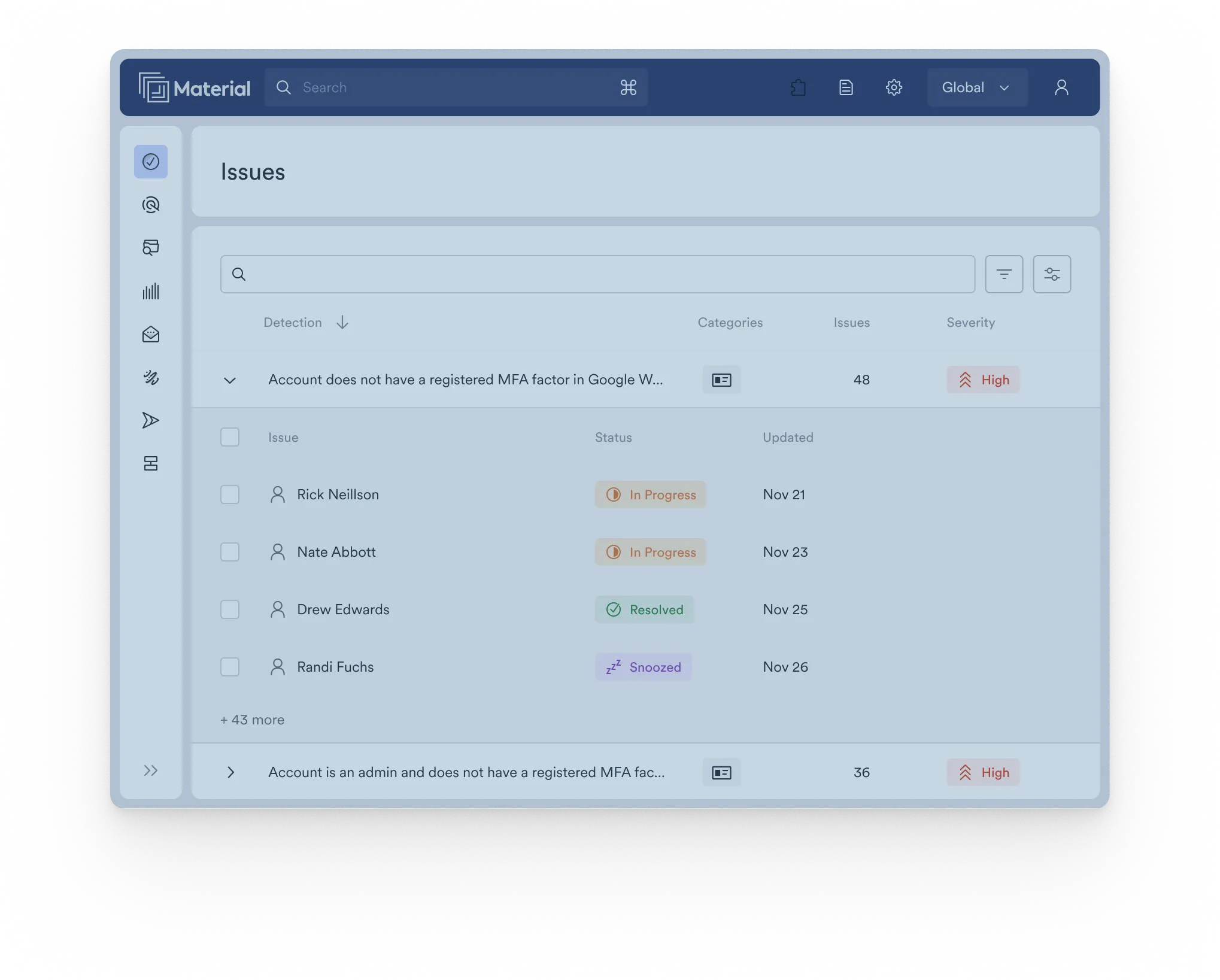
A cloud office security solution that automates detection and response across email, files, and configuration settings.
billed annually
All the features of Essentials with additional capabilities around data classification, governance, and protection.
billed annually
Enhance your security with advanced features that detect, respond to, and mitigate account takeovers. This functionality is available as an add-on or a stand-alone license.
billed annually
Find the Perfect Plan to Match Your Needs
Compare features, benefits, and pricing to choose the best option for your budget and goals.
Frequently Asked Questions
Find answers to common questions and get the details you need.
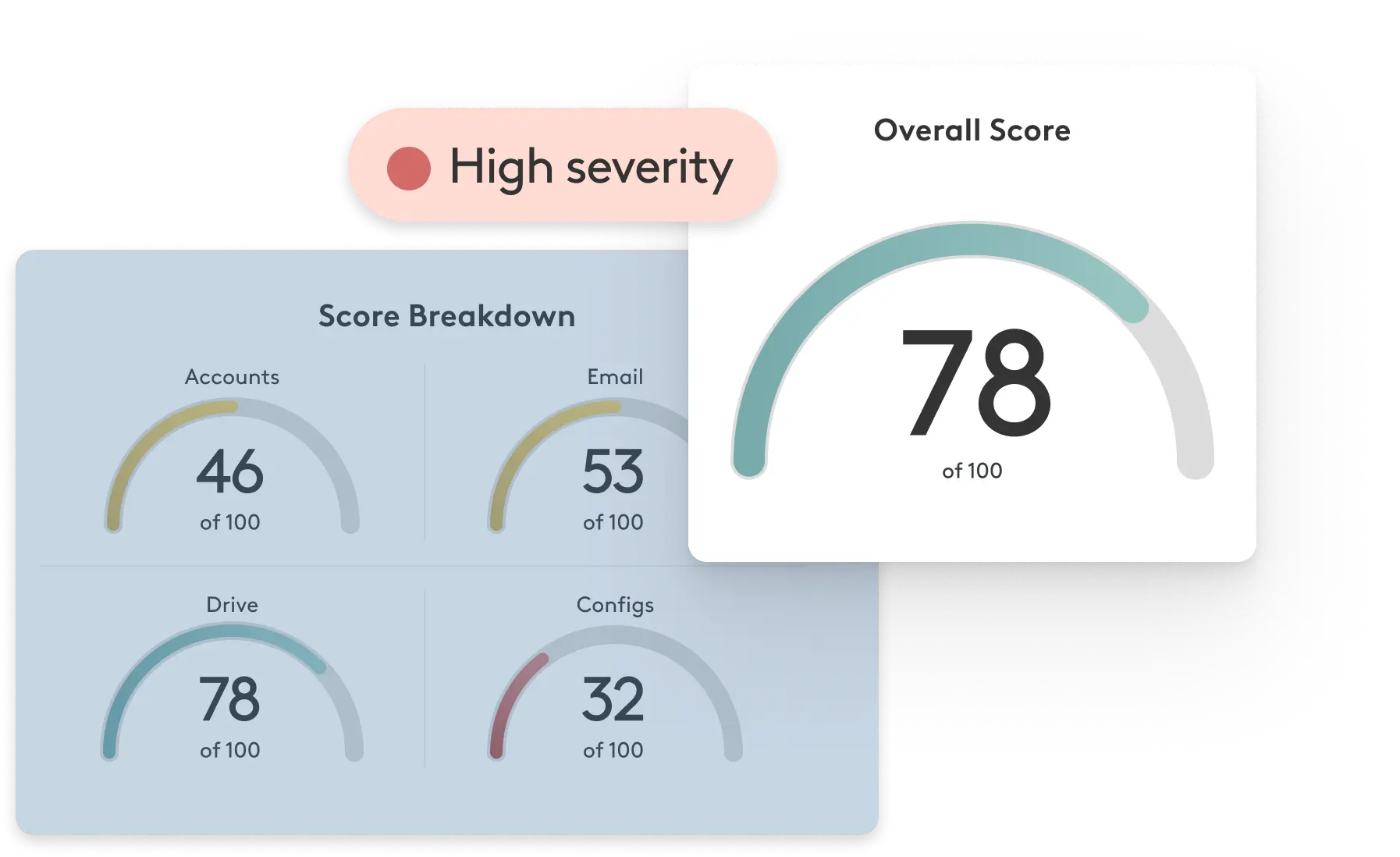
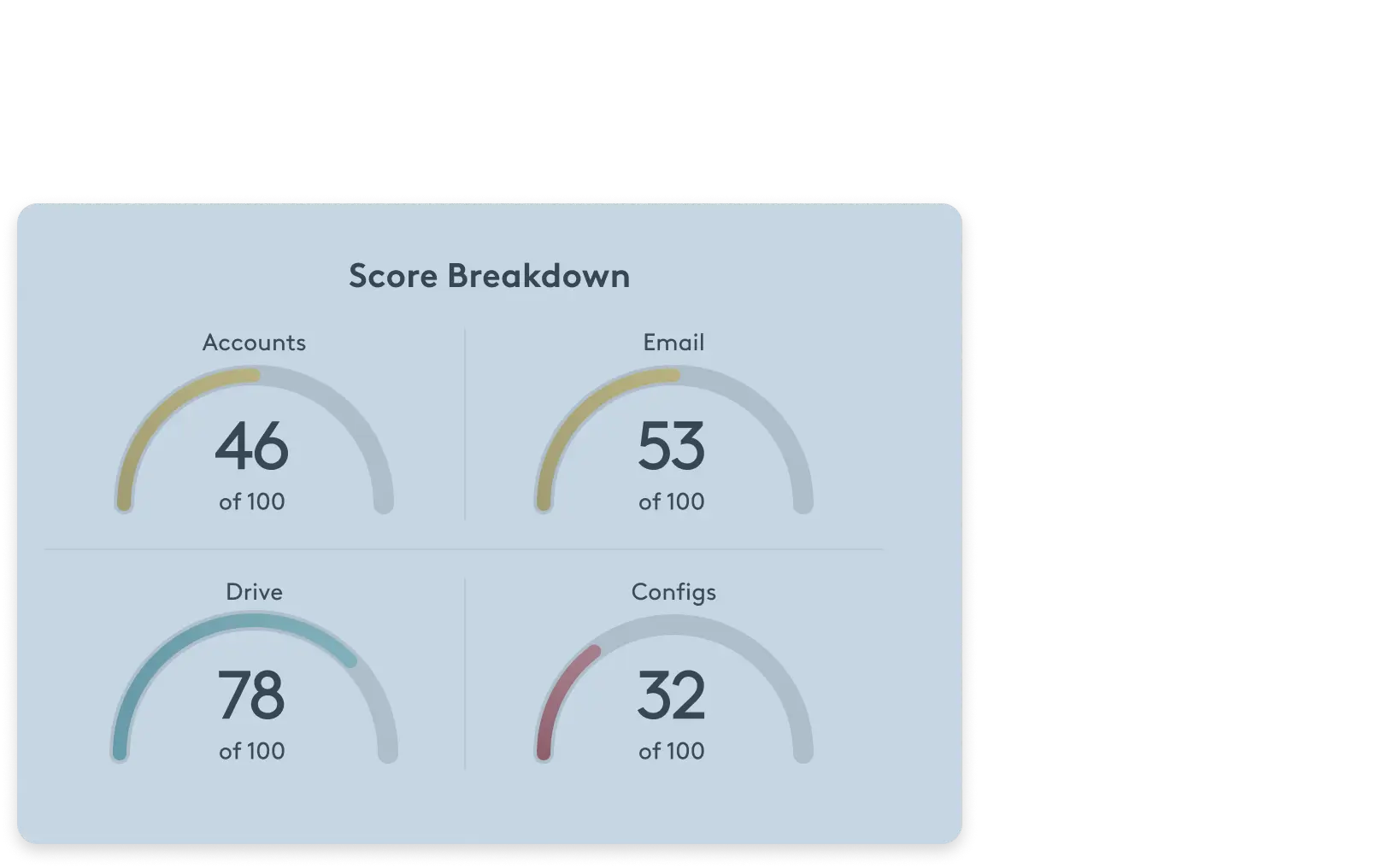
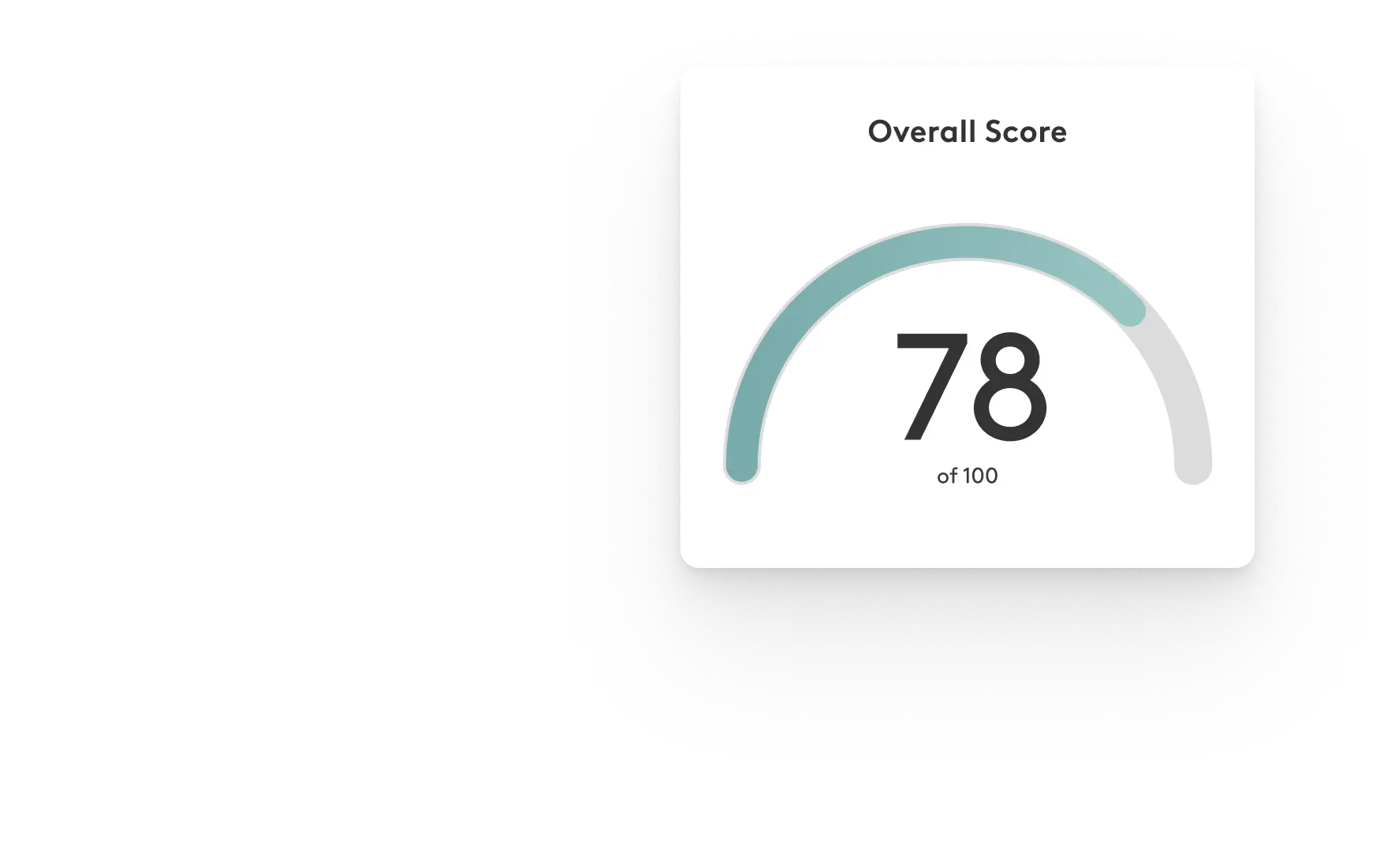
Check your Workspace security posture now
Material’s scorecard evaluates your approach to email, file, and account security, providing actionable recommendations to improve your security today. Stop guessing and evaluate now.