Material’s free Google Workspace Security Scorecard is designed to help organizations quickly assess their security posture across email, files, accounts, and global configurations, providing actionable recommendations to mitigate real-world risks.
Google Workspace is mission-critical infrastructure. It houses your organization's emails, documents, and accounts—the fundamental material your business runs on. But with that centrality comes complexity, and with complexity comes risk.
We've spent years protecting Google Workspace environments at scale, and we've seen the same security gaps appear across organizations of all sizes and industries. Configuration drift, overly permissive sharing settings, weak authentication policies, exposed sensitive information in inboxes and shared files, and subtle email security blind spots—these aren't theoretical vulnerabilities. They're the footholds attackers use to compromise real businesses.
The challenge isn't that security teams don't care about these risks. It's that Google Workspace security spans so many domains—email, files, identity, and global configurations—that it's difficult to maintain a complete picture of your posture, especially as your organization scales and your workspace evolves.
That's why we built a free Google Workspace Security Scorecard.
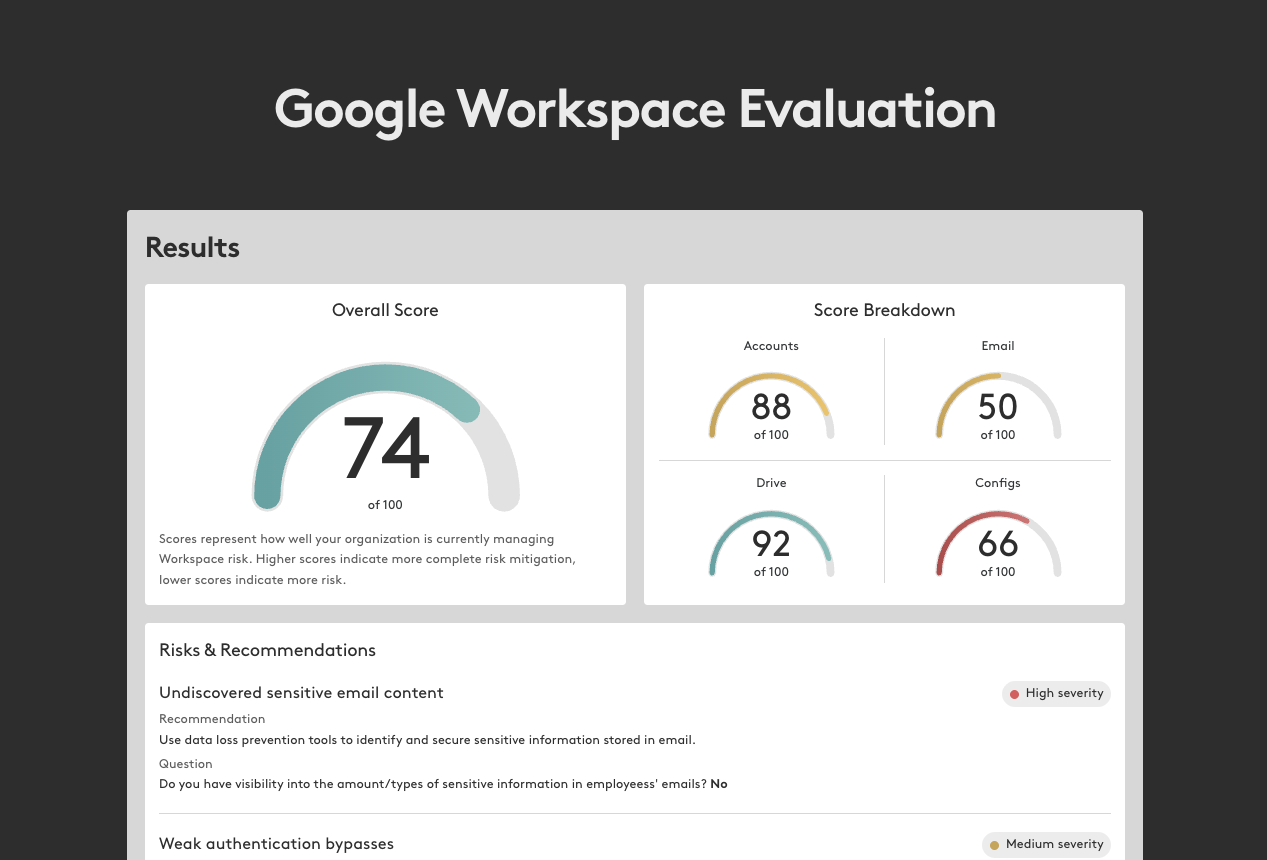
What the Assessment Covers
The self-assessment consists of 25 questions that examine security practices across four critical areas:
Email Security: How well is your inbox protected from phishing, business email compromise, and malicious messages that bypass native controls?
File Security: Are your Drive files and documents properly governed? How easily can you determine who has access to what, and what sensitive files are at risk of overexposure?
Account Security: How hardened are your user accounts against compromise? What happens when credentials are stolen or accounts are hijacked?
Global Configurations: Are your workspace-wide settings properly configured to reduce attack surface and enforce security policies?
Each question is based on real-world security incidents and misconfigurations we've observed protecting Google Workspace environments. The assessment doesn't require any technical integration or access to your workspace—just your knowledge of your current security practices.
What You'll Learn
When you complete the assessment, you'll receive:
- An overall risk score that benchmarks your current Google Workspace security posture
- Domain-specific risk scores for email, files, accounts, and configurations
- Detailed risk analysis for each answer that indicates potential vulnerabilities
- Actionable recommendations for improving your security posture in areas where you have exposure
The assessment is designed to be practical, not punitive. Our goal isn't to generate a failing grade—it's to help you understand where your risks lie and what you can do about them.
Why This Matters Now
Google Workspace attacks are becoming more sophisticated. Attackers know these platforms are critical infrastructure, and they've adapted their tactics accordingly. Phishing campaigns bypass traditional email security. Stolen credentials give attackers native access to your environment. Misconfigured sharing settings expose sensitive data. And because Google Workspace is designed for collaboration, the blast radius of a single compromise can be enormous.
The organizations that best defend against these threats aren't necessarily the ones with the biggest security budgets. They're the ones that understand their risk profile and address gaps systematically. This assessment gives you a clear starting point.
Take the Assessment
Whether you're a security engineer managing day-to-day workspace security, a CISO evaluating your organization's cloud security posture, or an IT leader responsible for Google Workspace administration, this assessment will give you actionable insights in just five minutes.
Take the Google Workspace Security Self-Assessment →
Your Google Workspace is what your business is made of. Make sure it's protected.

.png)
.png)


