Material's updates make it even easier for security teams to understand and respond to risks and threats with an overhauled Email Threats Dashboard, a new Account View, and more.
This quarter, we focused on helping security teams move faster from signal to story, seeing how attacks unfold, understanding where exposure lies, and acting decisively.
Two major updates lead the way: the overhauled Email Threats Dashboard and the new Account View. Together, they turn what used to be isolated insights into a connected picture of organizational risk.
The Overhauled Email Threats Dashboard
Email remains the most common way attackers get inside an environment. Our revamped Email Threats Dashboard gives defenders a deeper, more operational view of what’s happening (and why).
It’s now built to help prioritize, not just visualize. You’ll see not only how many threats were stopped, but how they break down by tactic, target, and trend.
It’s now built to prioritize, not just visualize. You’ll see not only how many threats were stopped, but how they break down by tactic, target, and trend.
What’s New
- Clearer prioritization. Compare blocked attacks across time to see where risk is rising.
- Deeper drill-downs. Filter by tactic, technique, or recipient to explain spikes or identify coordinated campaigns.
- Actionable visuals. Highlight patterns you can take directly into awareness training or detection tuning.
- Export-ready summaries. Share clean, executive-friendly insights without extra work.
- Detection Source & Efficiency Visualization. Understand where Material is catching suspicious messages automatically versus what’s being reported by users, and how those messages flow through classification outcomes.
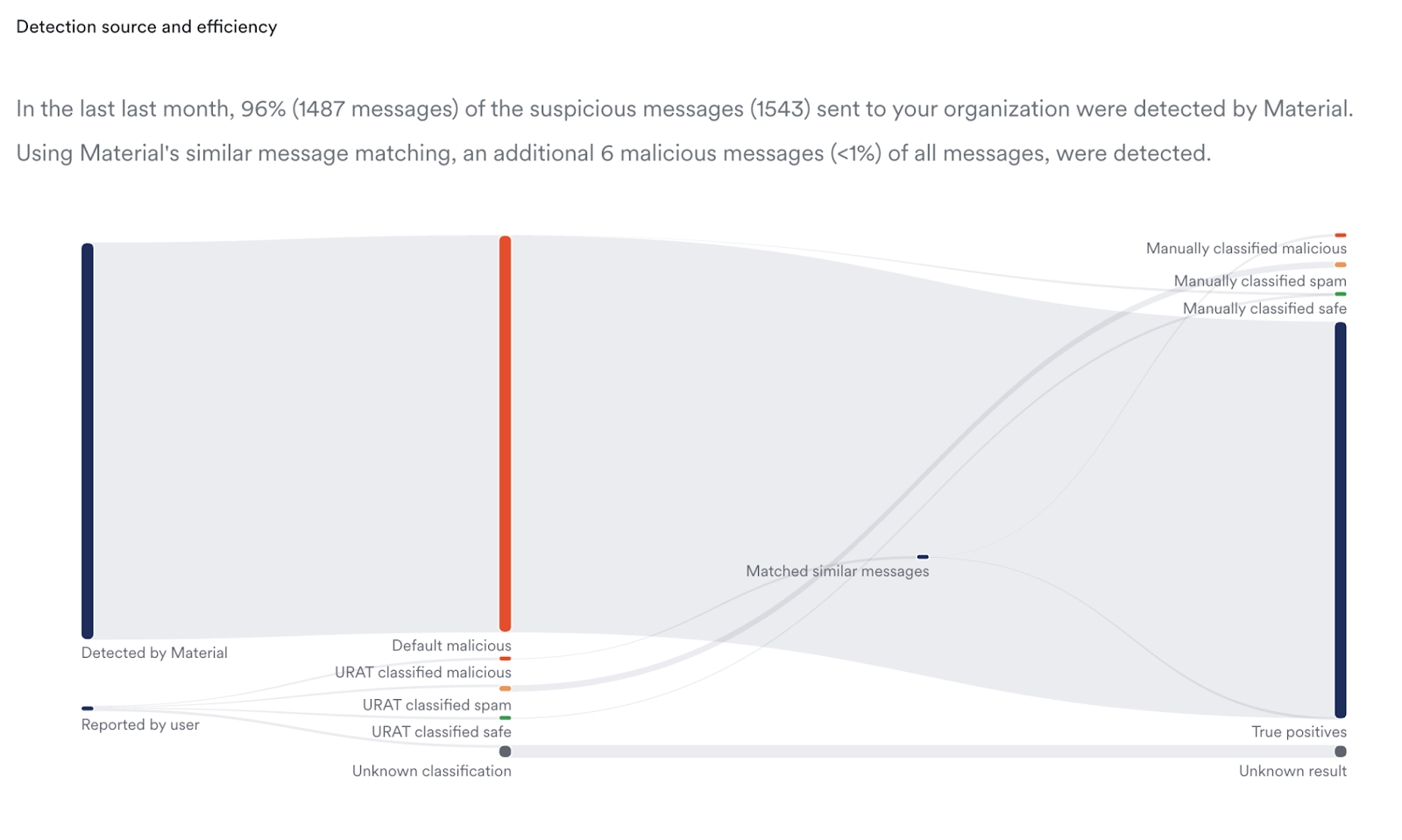
What Security Teams Are Saying
We rolled out the new dashboard to early-access customers, and the response has been clear: it’s changing how teams track and communicate risk.
“I pull this up weekly to check blocked attacks and patterns. The visuals are a noticeable improvement.” - Threat Analyst, Fintech Customer
“Substantially more powerful. I’m going to use this to show the value of Material.” - Detection & Response Lead, SaaS Customer
Even customers with sophisticated detection programs are using it to connect the dots between technical signals and executive reporting.
One detection engineer summarized it best: “It’s the first time I can tell the story of our email threats clearly, not just how many but who, when, and why.”
The New Account View
If the Email Threats Dashboard shows the big picture, the new Account View gives you the story behind each user.
Every account now has its own consolidated page, bringing together sign-in activity, exposure, detections, and remediation options.
Highlights include:
- Blast Radius summary to see potential spread from a compromised account
- Vulnerability overview with issue counts organized by severity
- Event timeline showing detections, investigations, and remediations chronologically
- Quick response controls to revoke sessions or update Material protections without switching tools.

This view was designed to help analysts move from “What happened?” to “What do I do next?” and do it in one place.
Dark Mode
Finally, just in time for spooky season, we’re rolling out a fitting treat for those who prefer things on the darker side: Dark Mode. Users can choose between Light Mode, Dark Mode, or a System Default option that automatically adjusts to your device’s settings. This update makes Material’s threat and risk insights more comfortable to view in any environment, whether you prefer a bright interface or a low-light display.
Why These Updates Matter
Security operators have enough noise. These updates focus on clarity: surfacing what’s important, removing what’s not, and making insights more immediately usable.
The Email Threats Dashboard helps you understand your exposure.
The Account View helps you act on it.
Together, they turn Material into a more connected, investigative workspace; one where you can see, explain, and respond faster.
Material is steadily expanding beyond email, bringing you a single, unified view of your organization’s risk surface: inbox, documents, accounts, and more. Our goal remains the same: help security teams see, understand, and act faster (without adding noise).
To see Material's updates for yourself, contact us for a demo today. If you're not sure about how strong your Workspace security posture is, check out our Workspace Security Scorecard self-assessment.

.png)
.png)
.png)

