Material secures email, inside and out
Blocking inbound threats is critical–but it’s no longer enough. It’s time for a complete approach to email security.

-svg.svg)

%20(1)-svg.svg)
.svg)
-svg.svg)


-svg%20(1).svg)





%20(2).avif)

.svg)





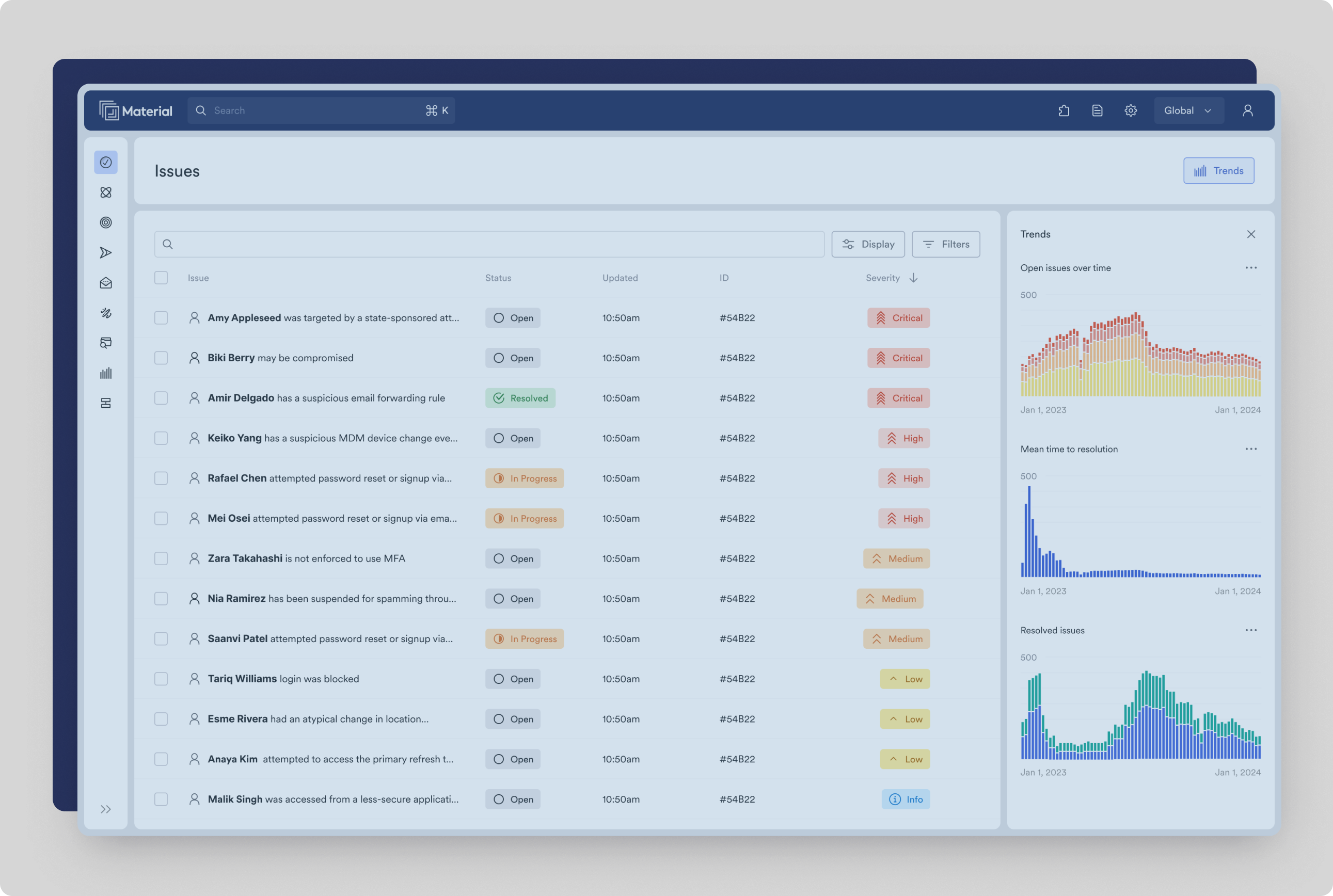
Stop threats that evade native defenses
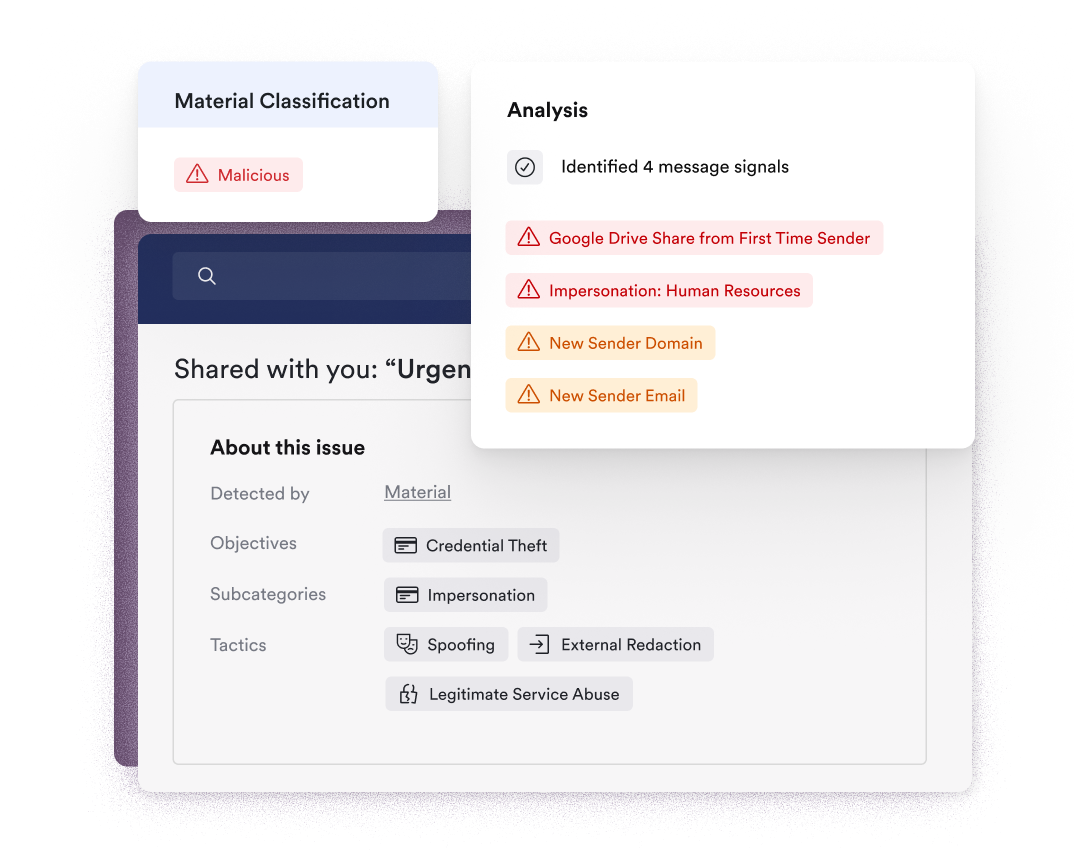
Material stops VIP impersonations, BEC attacks, and other sophisticated attacks that slip past native defenses with a combination of AI, threat research, and organizational context – without your analysts needing to lift a finger.
.png)
Protect the inbox from account takeovers
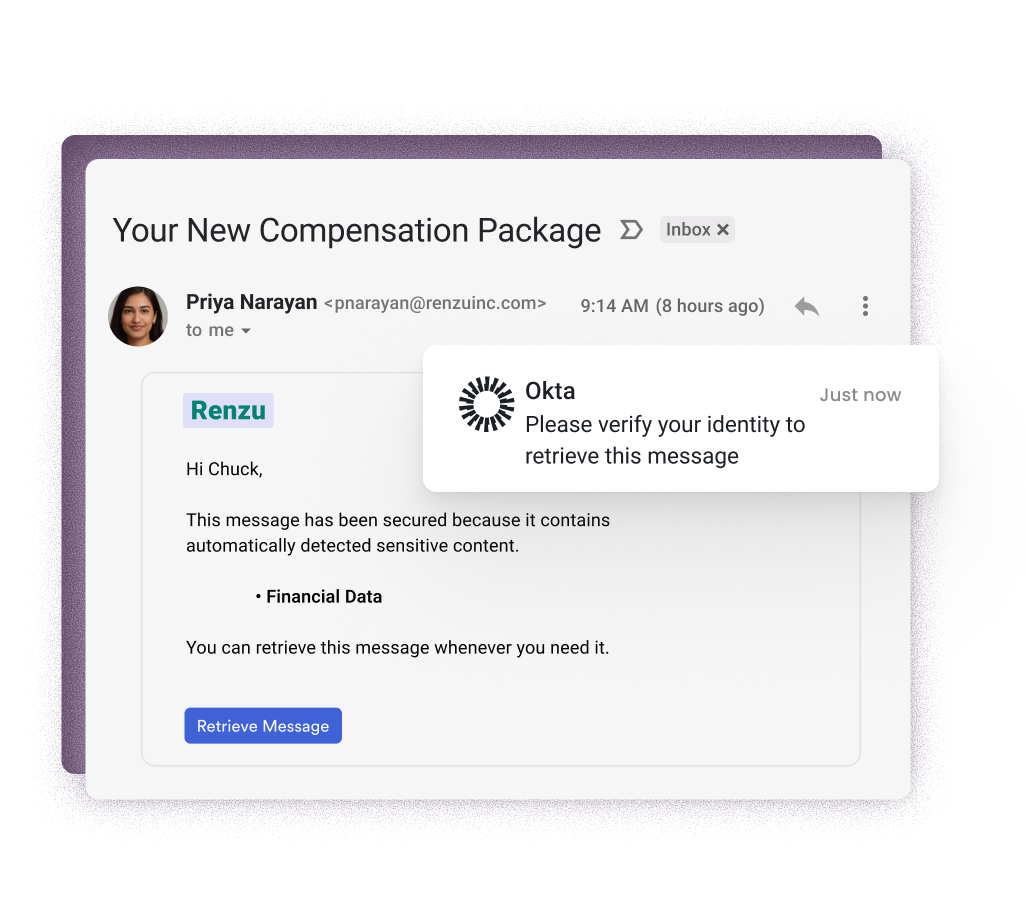
Material contains email account takeovers by combining unique message-level data protection, configuration monitoring and behavior analysis with automated remediation. Email account compromises are the biggest identity threat facing organizations today, and Material detects them and minimizes their blast radius faster than anyone else on the market.
Automate threat response and reduce analyst toil
Material automates the entire email threat lifecycle, from user report through remediation. Similarity matching and herd immunity immediately protects your entire user base from the first report or detection, while Material’s built-in AI with agentic behavior saves security teams hours of manual triage work.
.png)
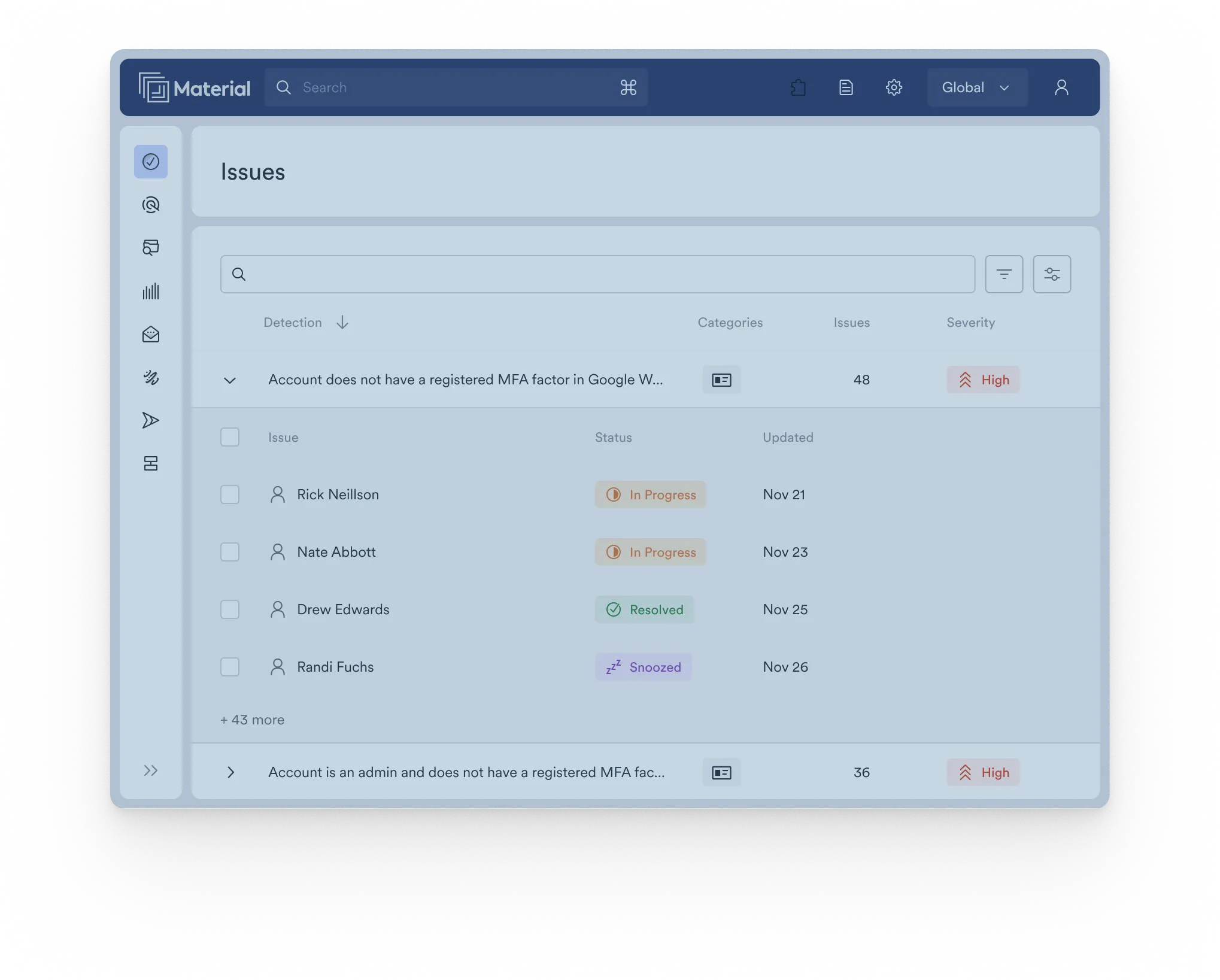
Detect and respond to threats across the entire cloud office
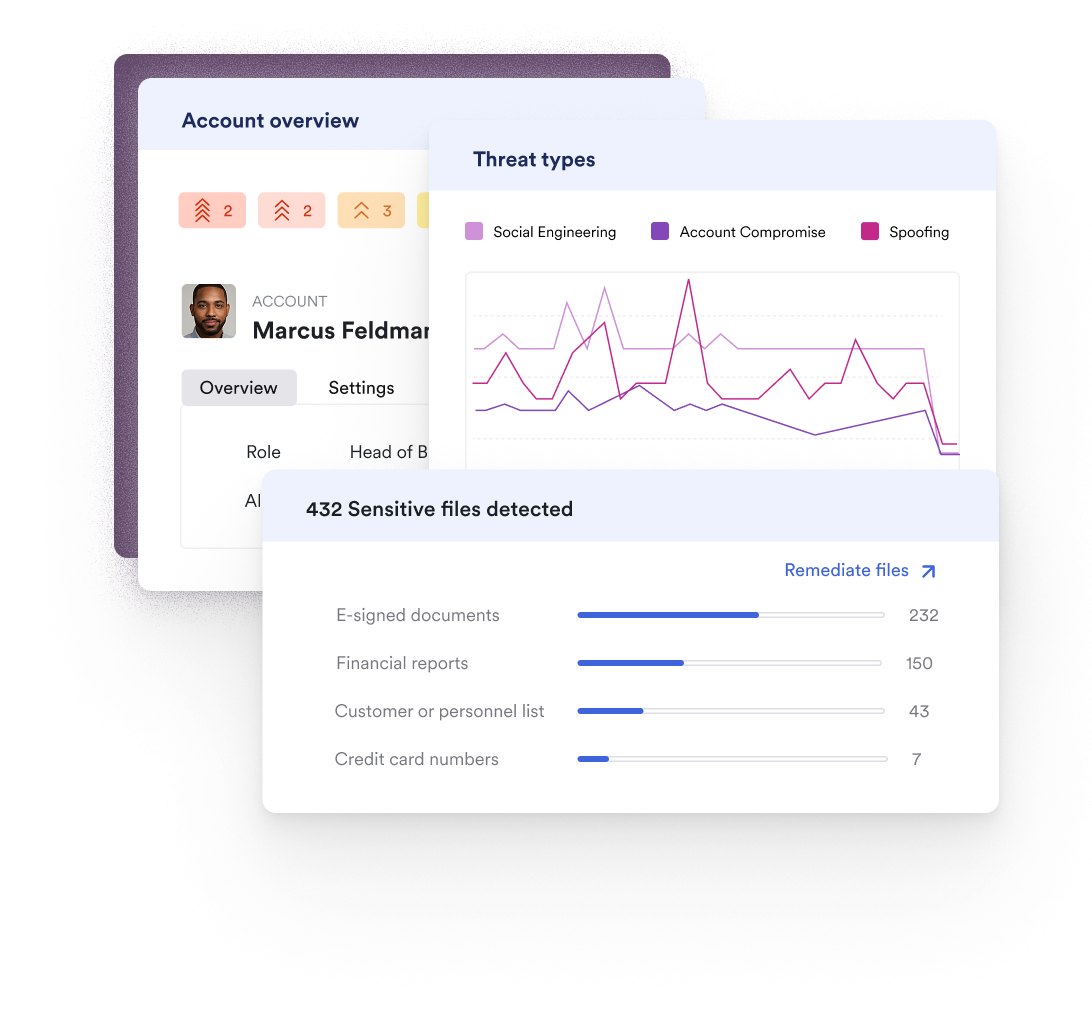
Material is the first detection and response platform built for the entire cloud office: signals from files and accounts provide context for email alerts and vice versa, providing richer context and enabling detection of subtle risks and threats that other tools miss.
.png)

Email security: evolved
Protect your email from the outside in while safeguarding the entire cloud office from the inside out. Inbound defense combined with data protection and identity threat response provides holistic security.
Email Security
Automatically detect and remediate malicious emails that bypass native controls
File Security
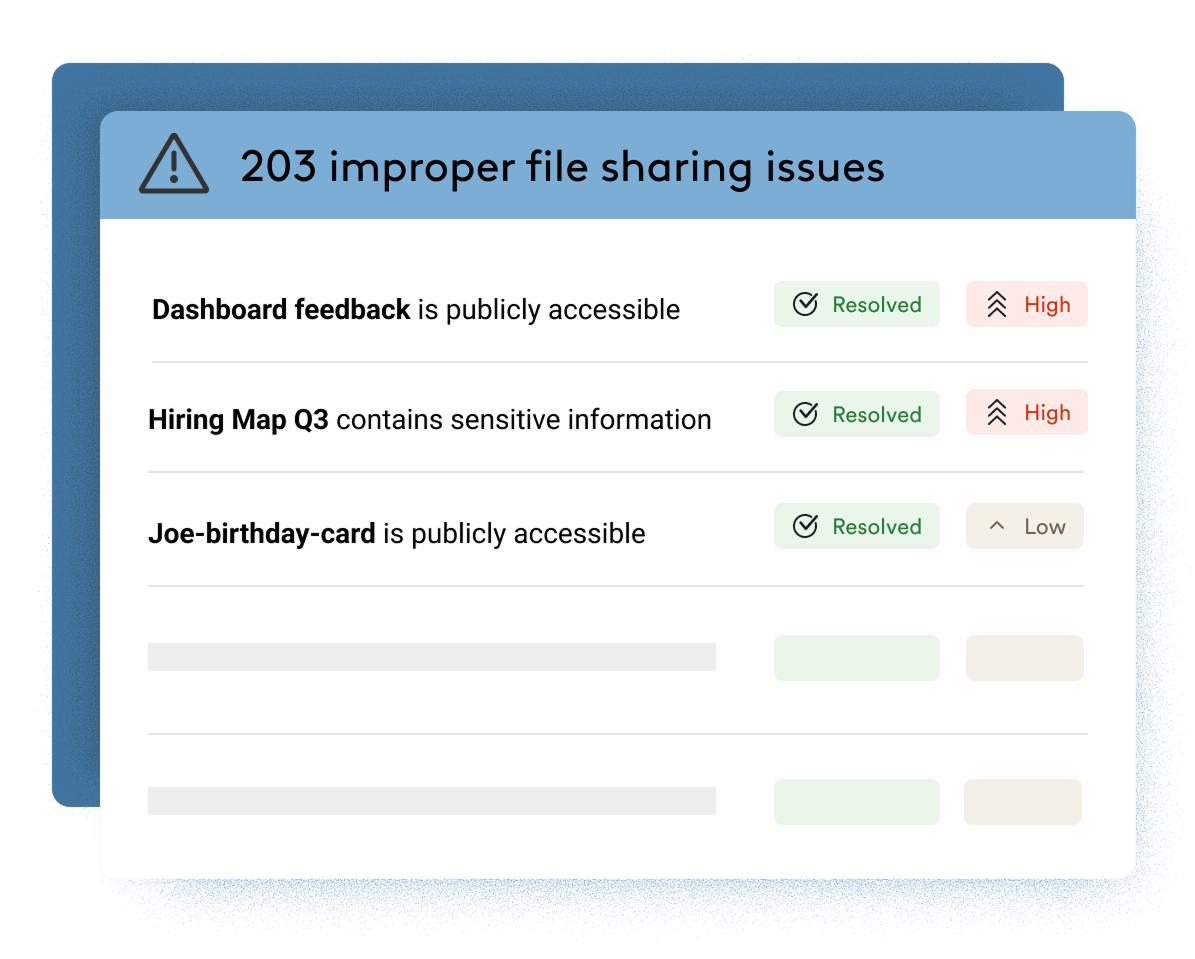
Automatically protect sensitive data at scale without hampering productivity & collaboration (Shared Drives and MyDrives)
Account Security
Automatically monitor and remediate against ATOs, while finding and fixing misconfigurations
Explore relevant use cases
Stop BEC and VEC Attacks
Detect and prevent Business Email Compromise and Vendor Email Compromise attacks.
Automate User Report Response
Transform user-reported phishing into instant protection while eliminating toil.
Detect and Protect Sensitive Email Data
Bring a true zero trust approach to email without slowing down your business.
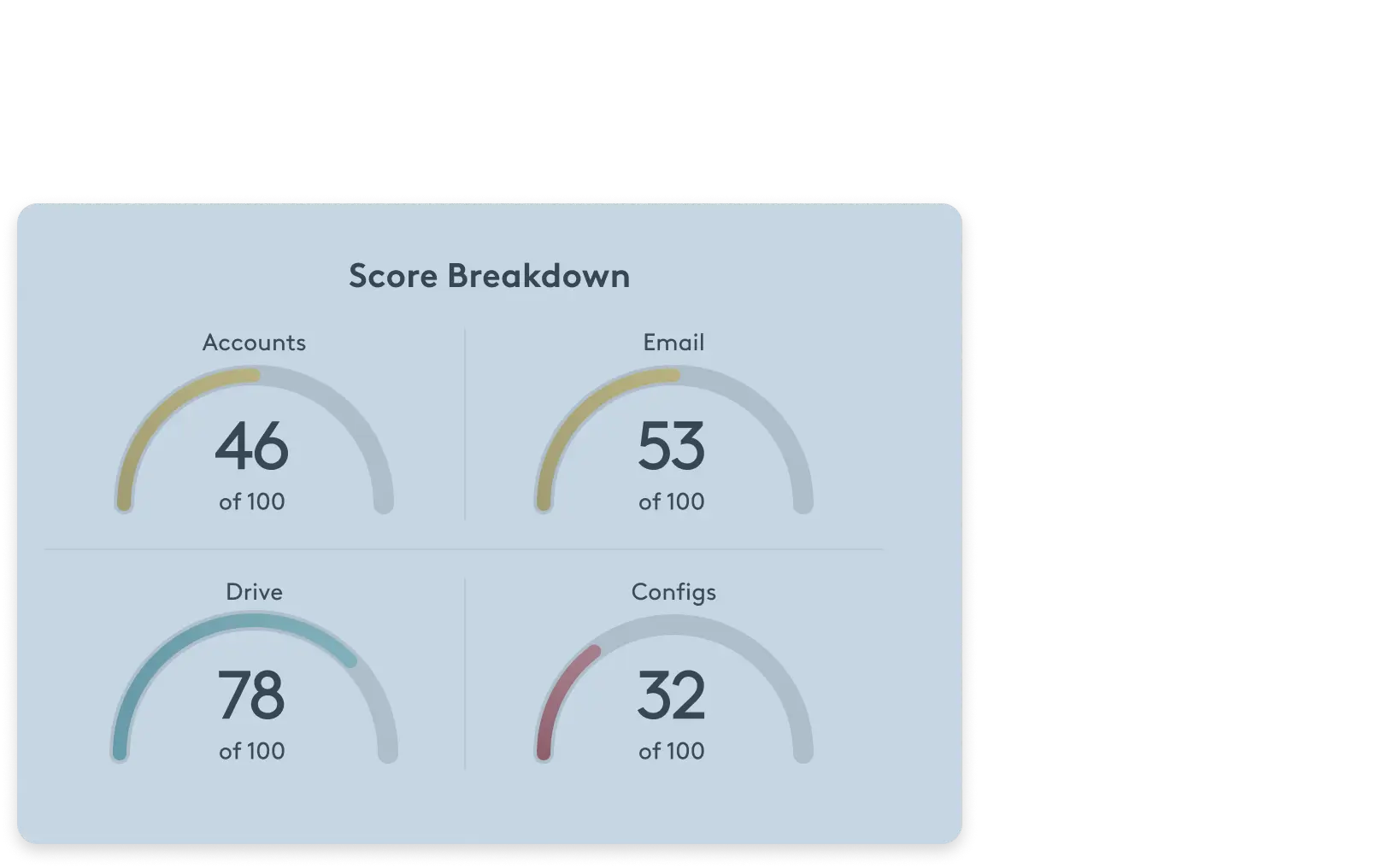
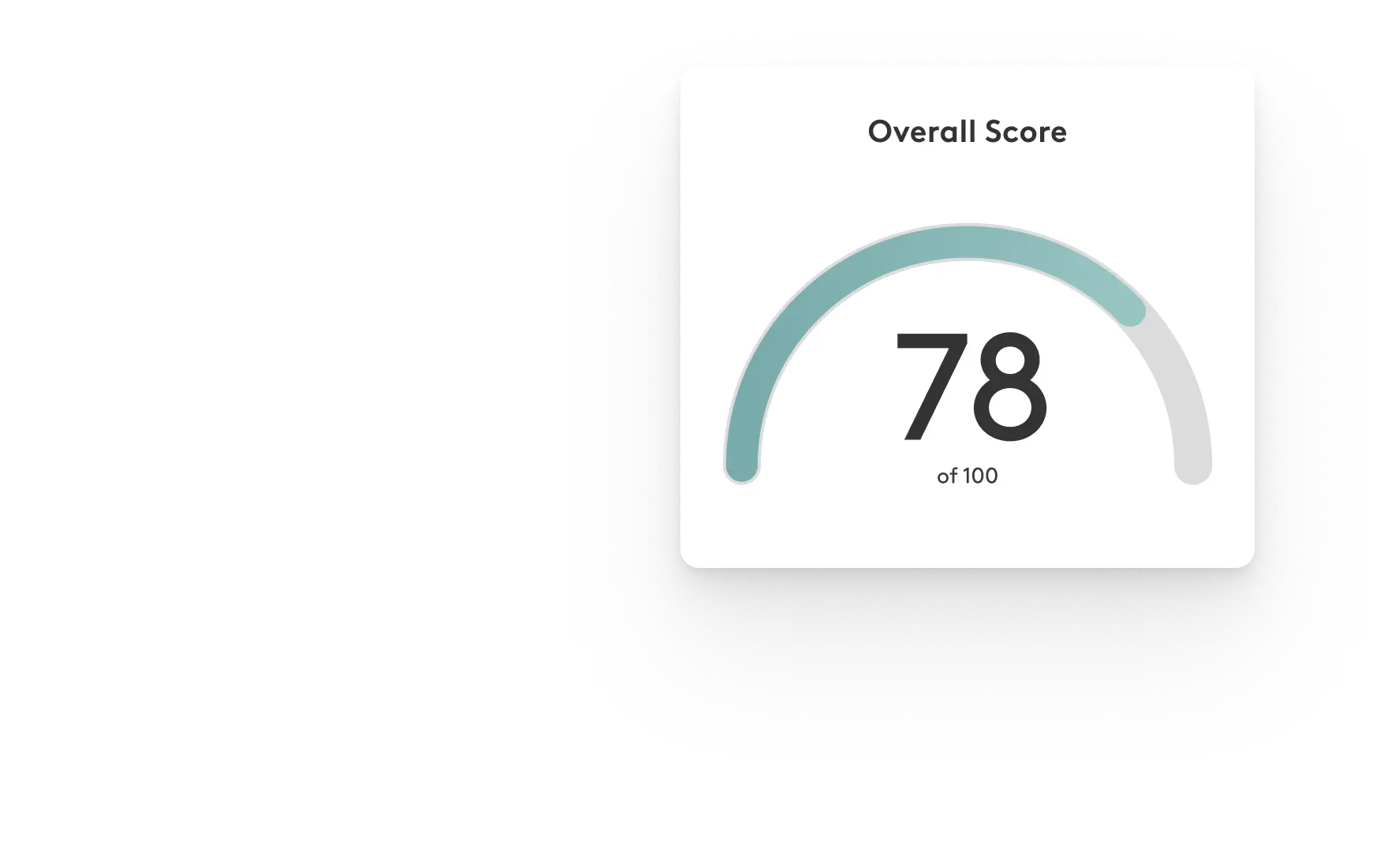
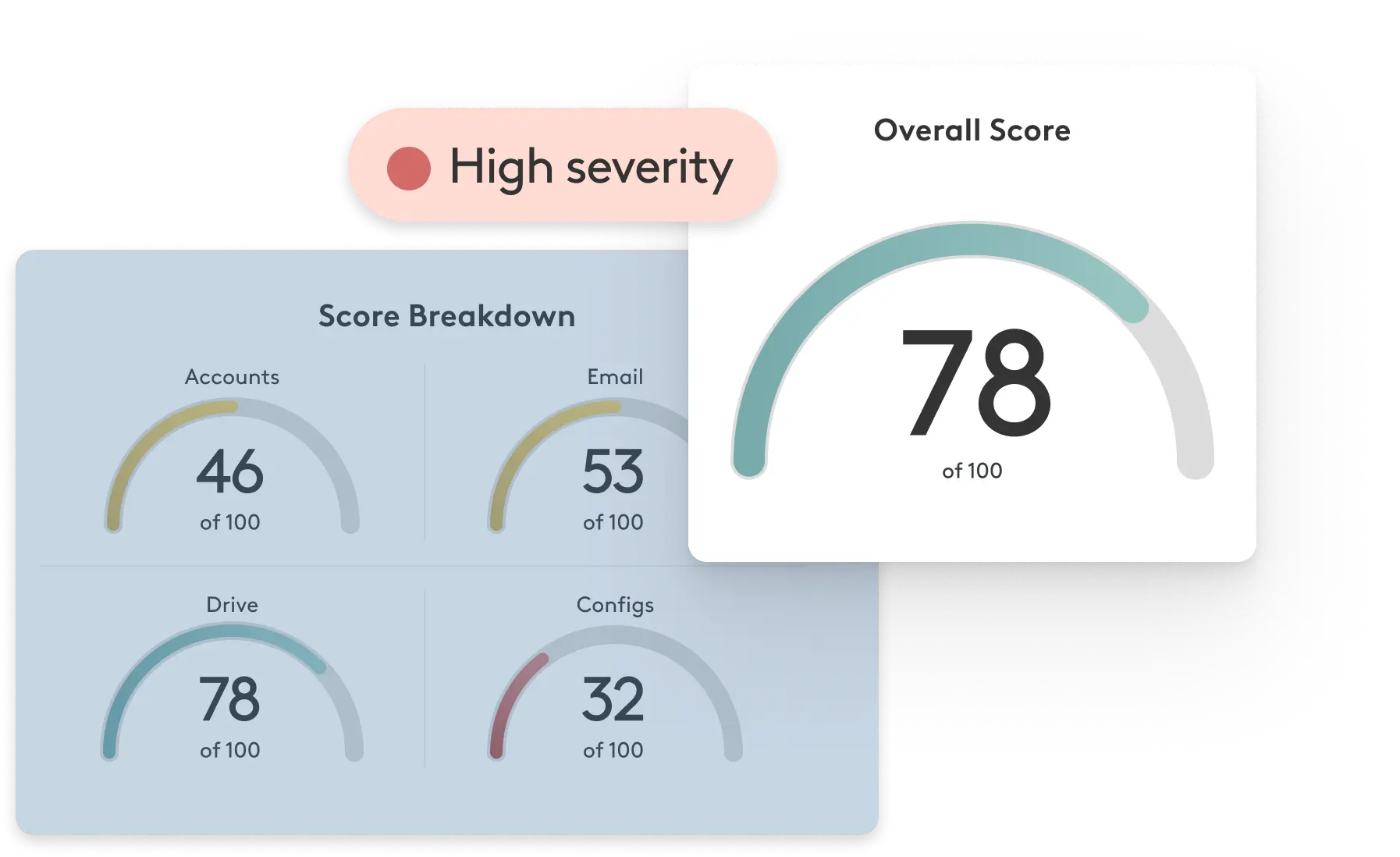
Check your Workspace security posture now
Material’s scorecard evaluates your approach to email, file, and account security, providing actionable recommendations to improve your security today. Stop guessing and evaluate now.

%20(1).avif)
.png)



.png)

.png)