Material Hardens your Identities and Contains ATO Attacks
Your users’ accounts are the keys to your kingdom. Protect them with unmatched visibility and automated identity threat detection and response.
.svg)
-svg.svg)

%20(1)-svg.svg)
.svg)
-svg.svg)


-svg%20(1).svg)





%20(2).avif)

.svg)





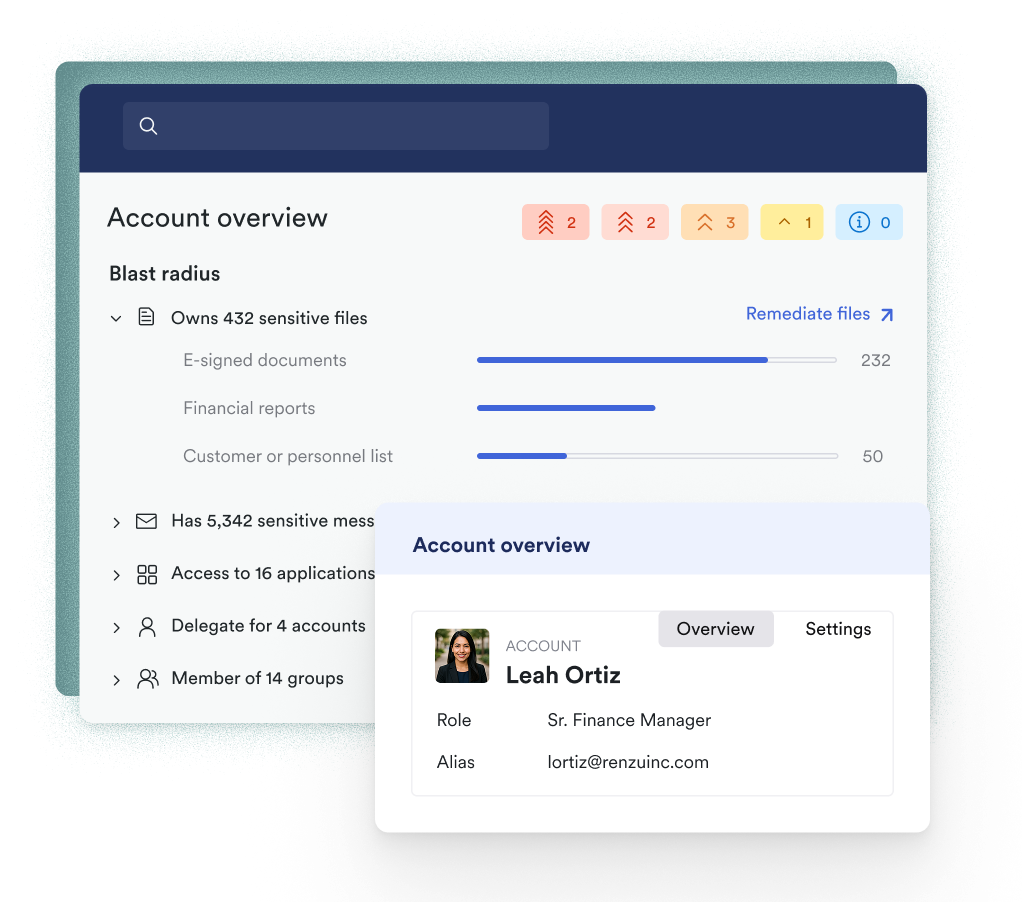
Unify identity and data risk posture
The platform breaks down security silos by connecting a user’s identity posture with the sensitivity of the data they can access, providing unmatched context to identify and prioritize the most critical risks.
.png)
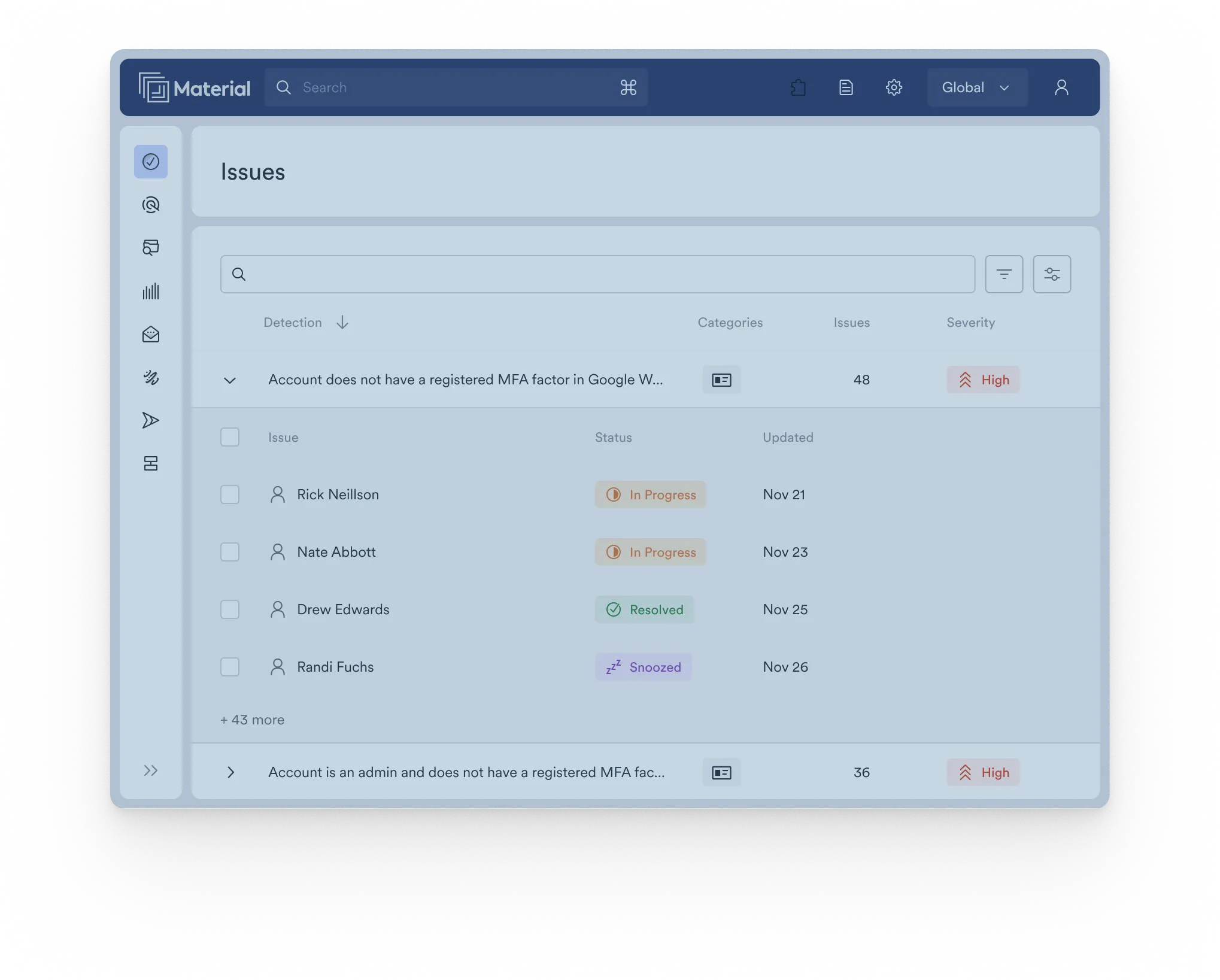
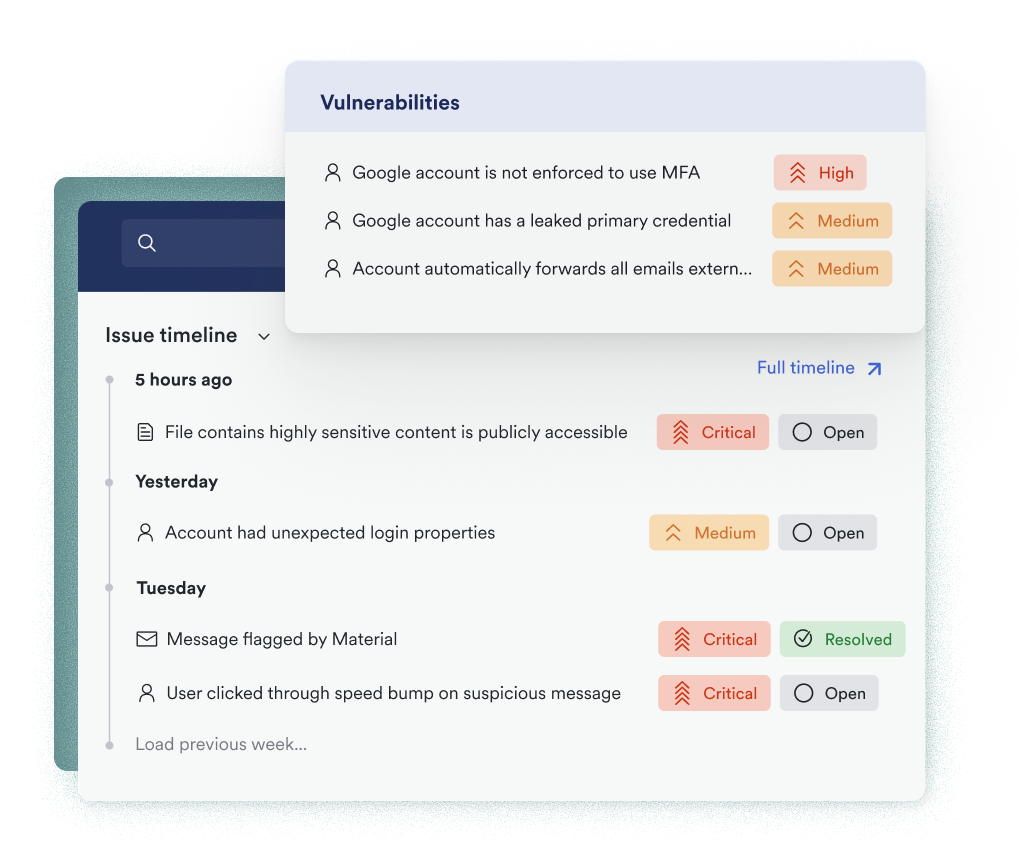
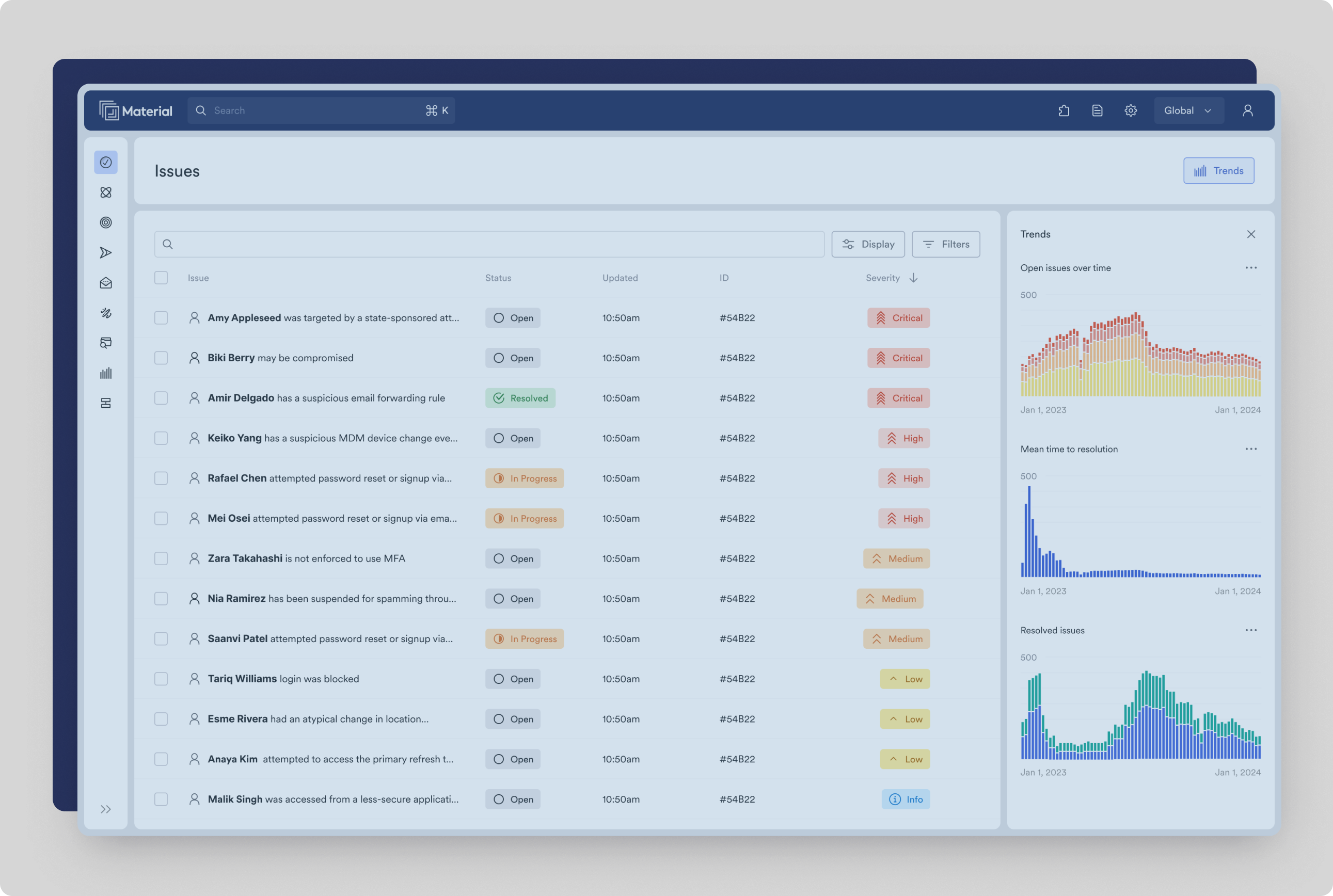
Detect account takeovers early
Material monitors a range of signals from across the cloud office, from suspicious forwarding rules to insecure email connections and much more, catching and correlating signals and IOCs other platforms miss to detect compromised accounts quickly.
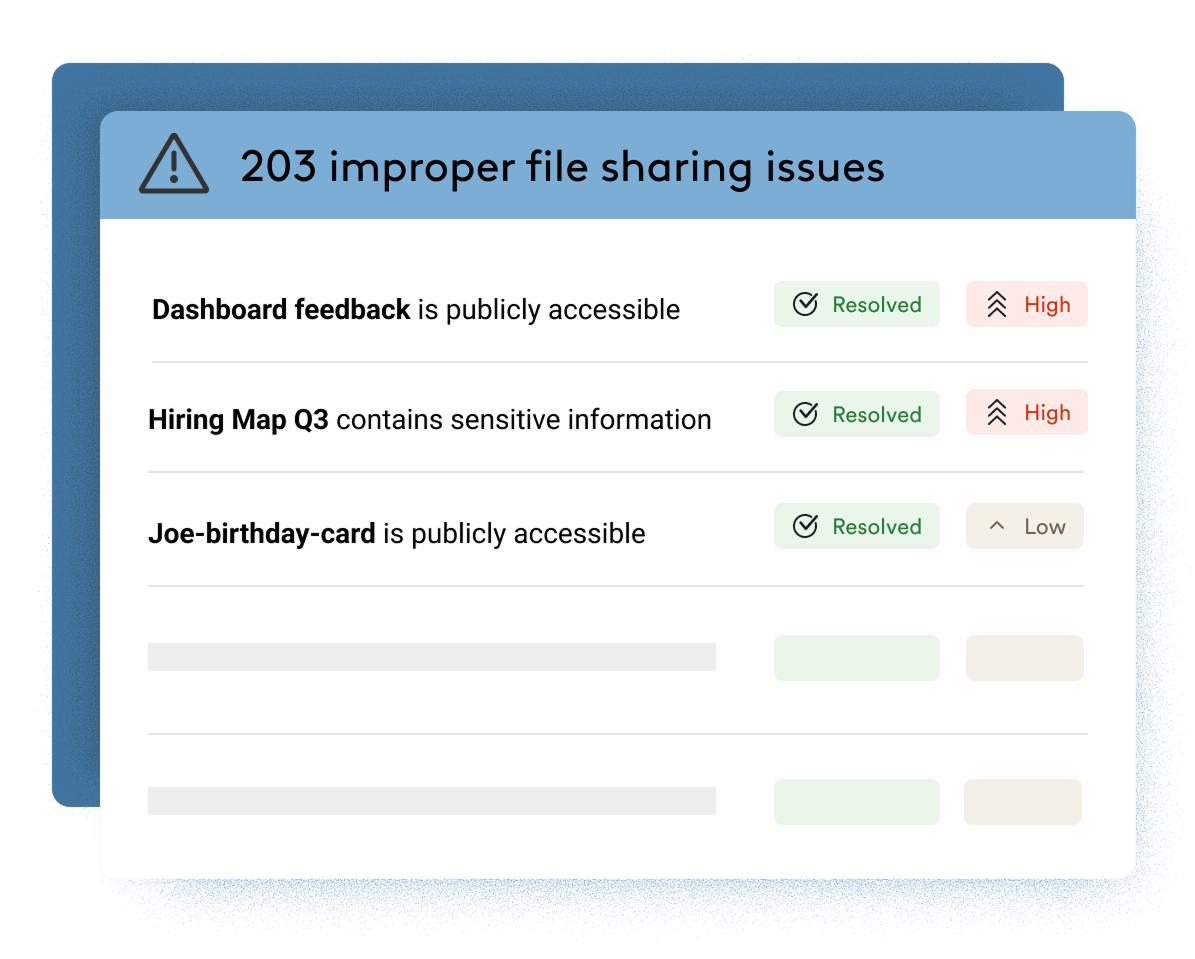
Limit the blast radius of a compromised account
The platform assumes compromise and prevents attackers from accessing the most sensitive information in a breached account. Automatically limit avenues for lateral movement, persistence, and evasion.
.png)
Detect and respond to threats across the entire cloud office
Material’s comprehensive visibility into your entire cloud office gives unmatched insights into the security of your accounts–from settings and configurations to inbound email threats.
.png)

.png)
Protect your critical identities
Continually monitor for even the most subtle signs of account takeovers while actively protecting against data exfiltration and lateral expansion.
Email Security
Automatically detect and remediate malicious emails that bypass native controls
File Security
Automatically protect sensitive data at scale without hampering productivity & collaboration (Shared Drives and MyDrives)
Account Security
Automatically monitor and remediate against ATOs, while finding and fixing misconfigurations
Explore relevant use cases
Contain Account Takeovers
Quickly detect and contain unauthorized access to limit the damage of a breach.
Automatically Prevent Configuration Drift
Proactively manage your Google Workspace and Microsoft 365 security posture.
Control Shadow and Unauthorized AI
Gain visibility and control over third-party app usage to manage shadow AI and IT.
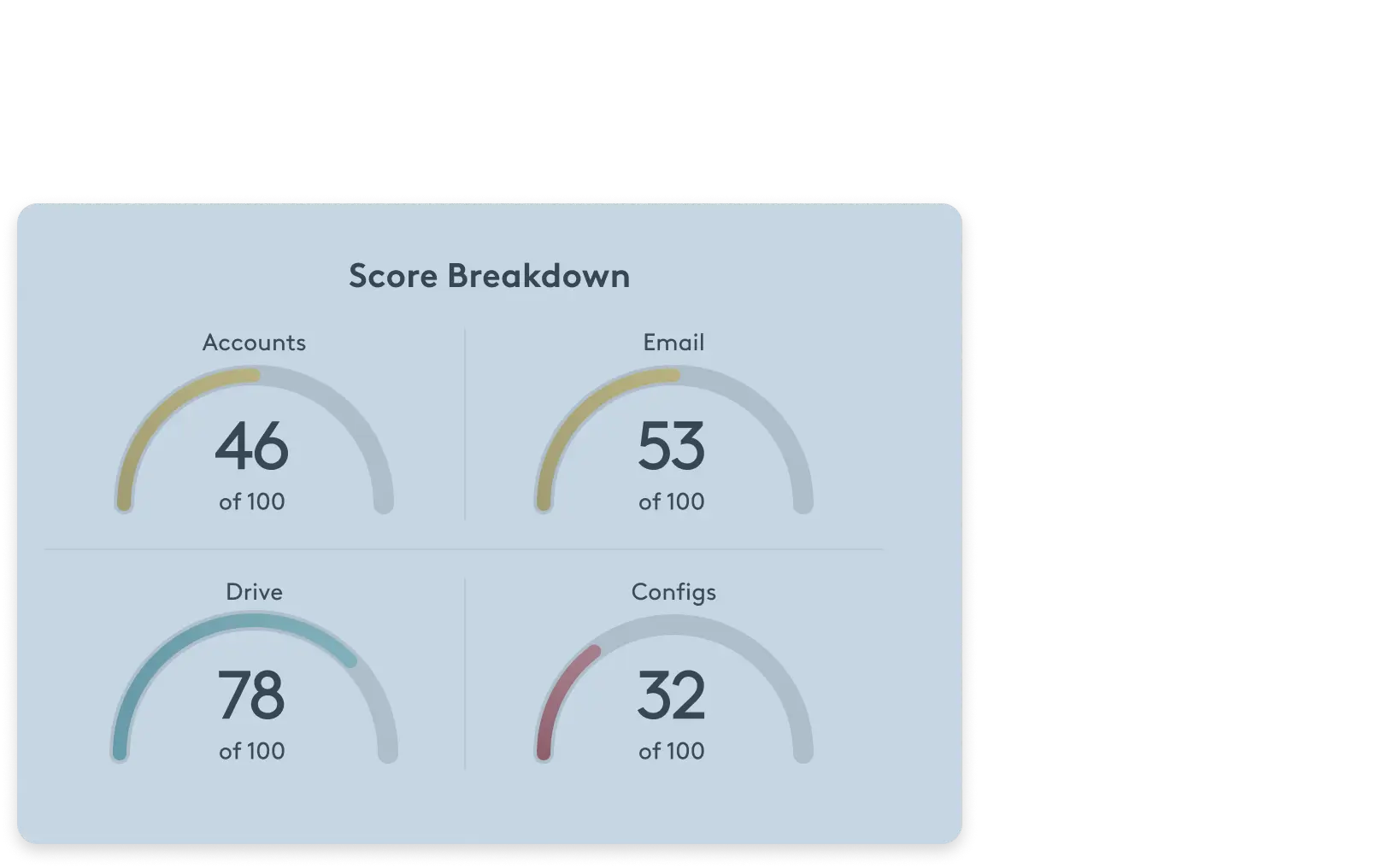
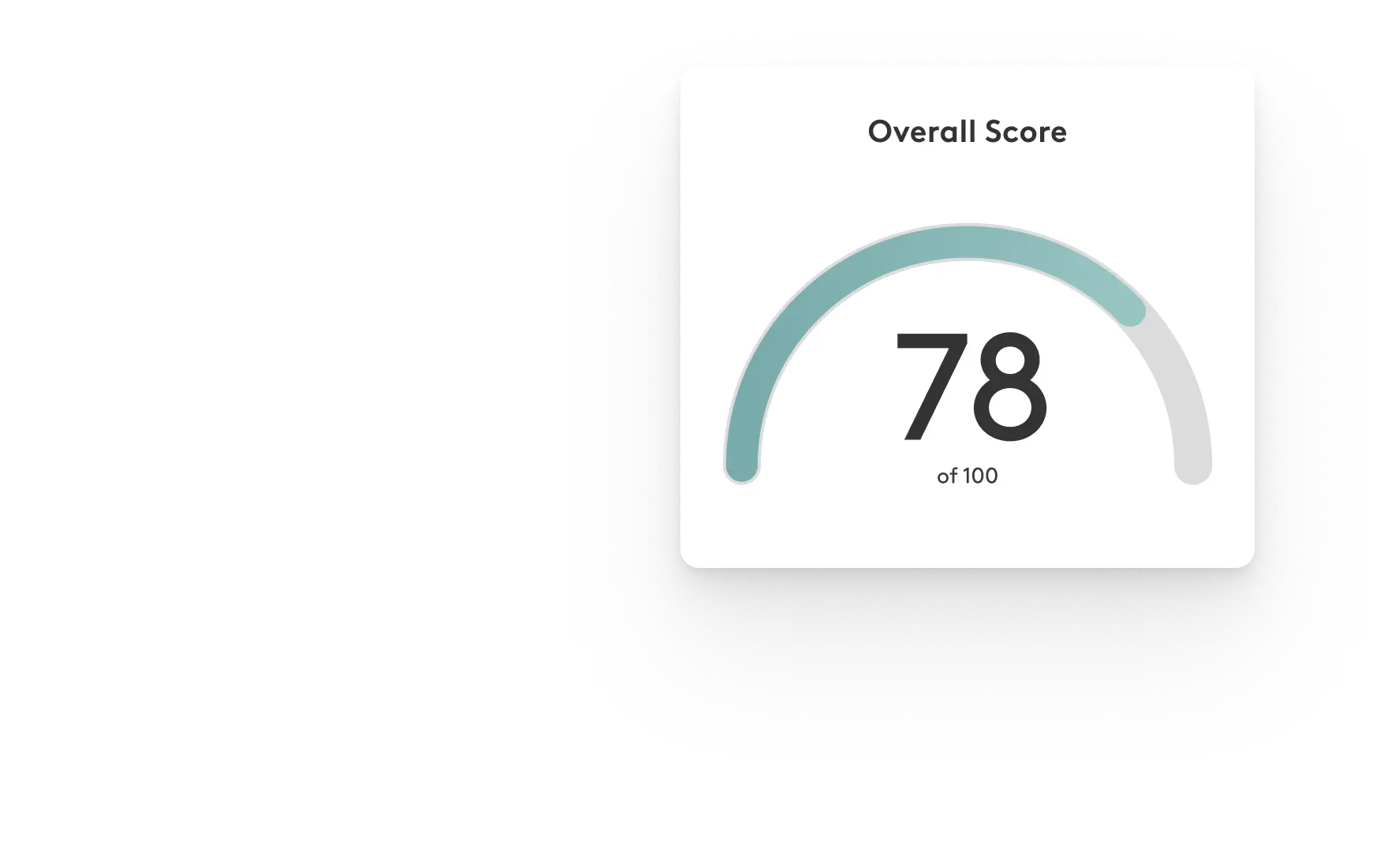
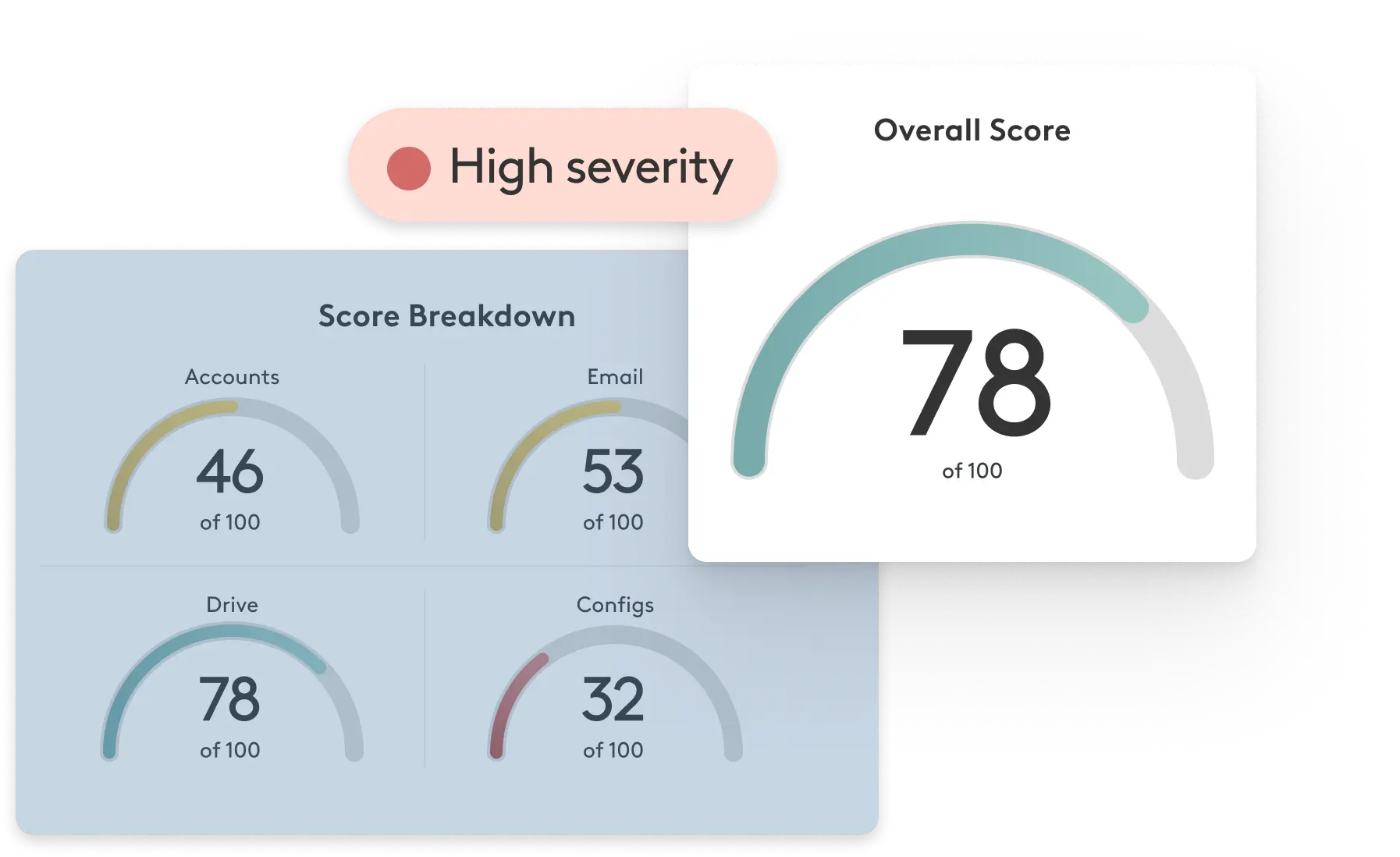
Check your Workspace security posture now
Material’s scorecard evaluates your approach to email, file, and account security, providing actionable recommendations to improve your security today. Stop guessing and evaluate now.

.png)
.png)

.png)
.png)

.png)
.webp)