One platform to secure the cloud workspace
Material is a dedicated security platform for Google Workspace and Microsoft 365—the critical infrastructure organizations run on. Stop attacks, protect sensitive data, and strengthen your security posture with one solution built for modern security and IT teams.

Protect your entire cloud workspace with a single platform
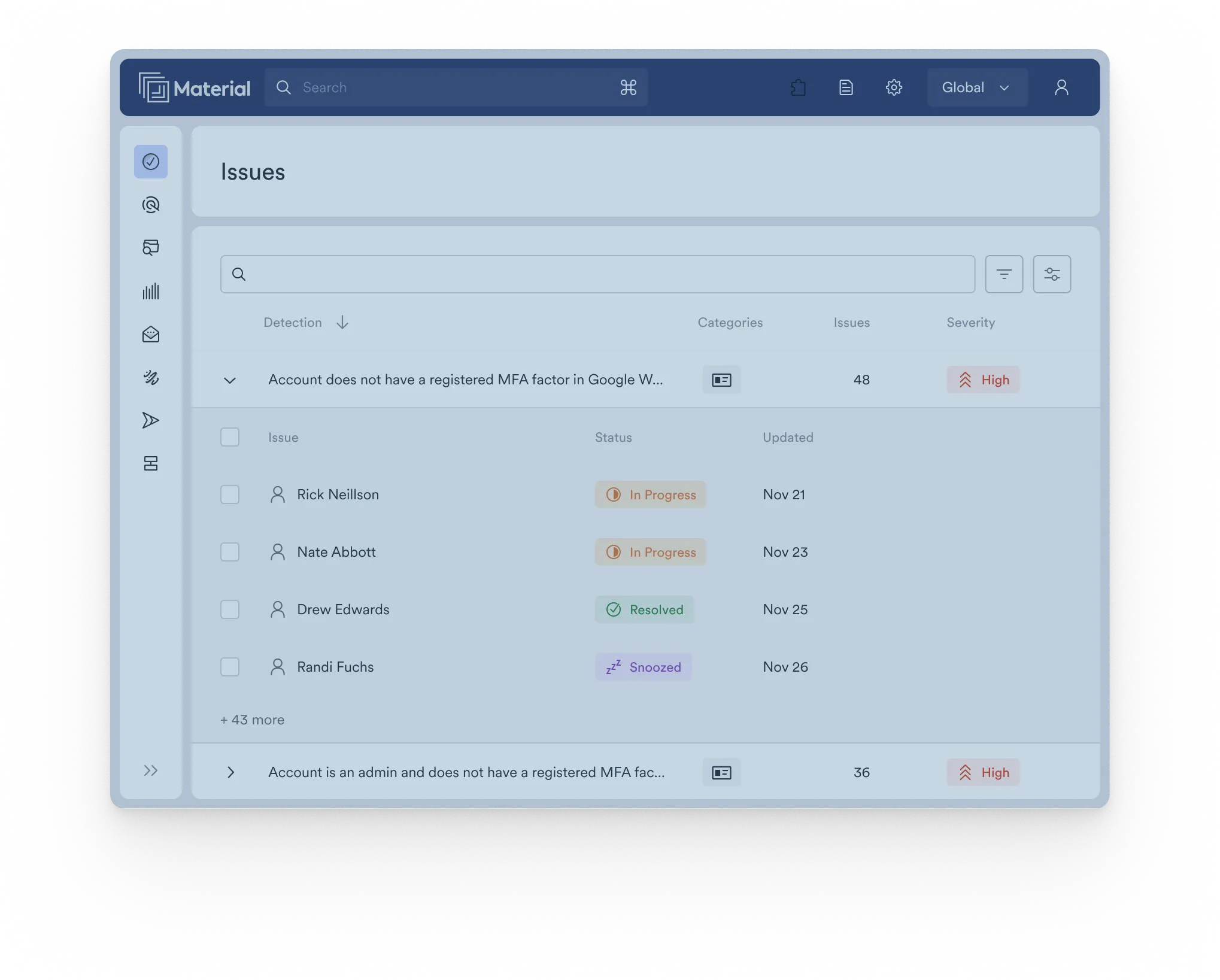
Point solutions and home-grown detections create gaps and drain efficiency. Material replaces the patchwork with a single platform that combines threat detection and response across email, files, and accounts—so you can get more done with fewer resources.
Email Security
Material runs on auto-pilot to remediate sophisticated email attacks that bypass traditional controls—without disrupting operations or wasting resources managing rulesets. It also automates user report triage with AI-powered investigation and response workflows.
.png)
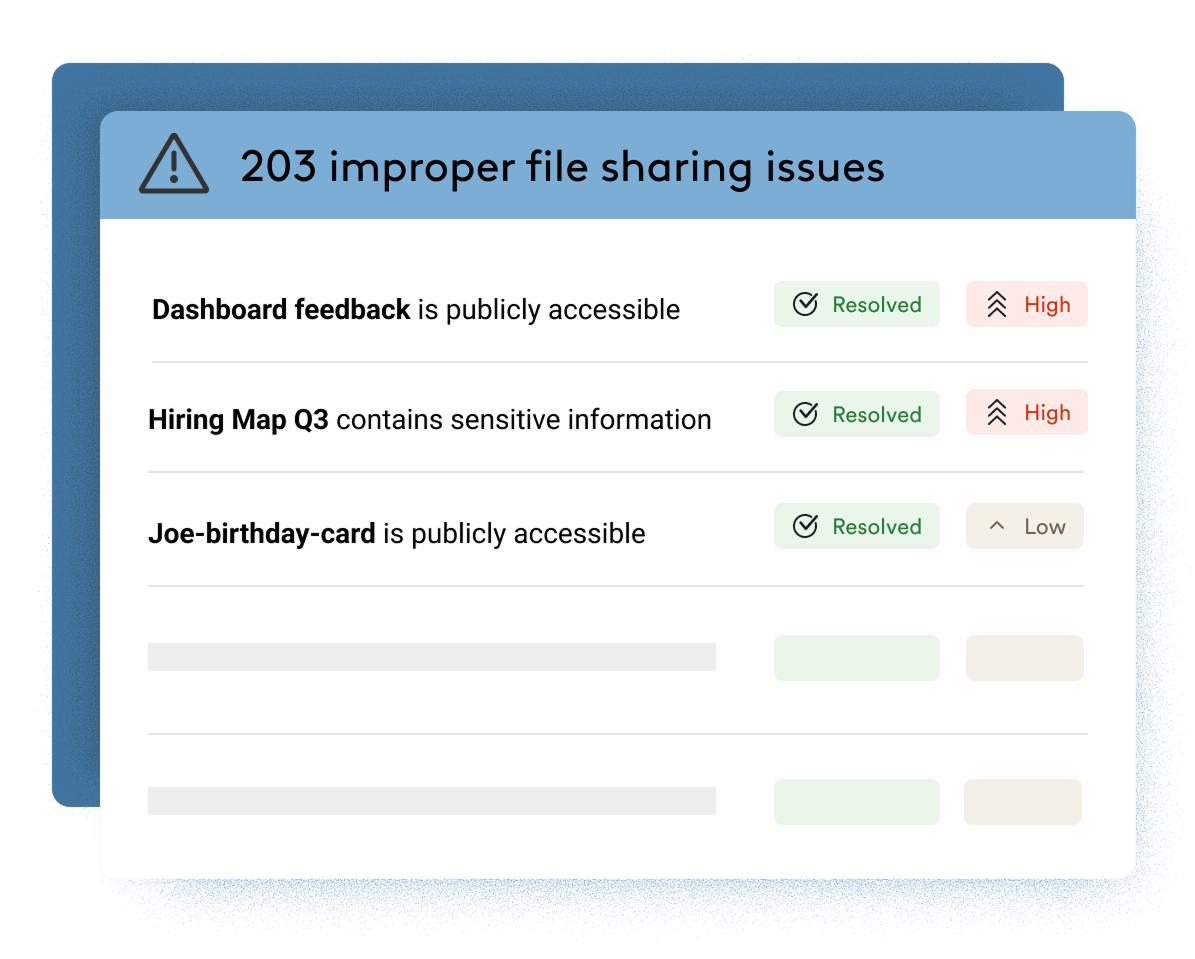
File Security
Understand where sensitive data exists, if it is exposed, and reduce the risk. Material detects sensitive content in files and includes tools to automatically remediate excessive permissions and inappropriate sharing–without hampering collaboration or slowing your team down.
Account Security
Detect account takeovers, contain their impact, and proactively harden your accounts. The breadth and depth of Material’s integration with the cloud office prevents attackers from establishing and expanding a foothold, moving laterally, and exfiltrating data.
.png)
Built for the way you work
The most innovative organizations trust Material
-svg.svg)

%20(1)-svg.svg)
.svg)
-svg.svg)


-svg%20(1).svg)





%20(2).avif)

.svg)





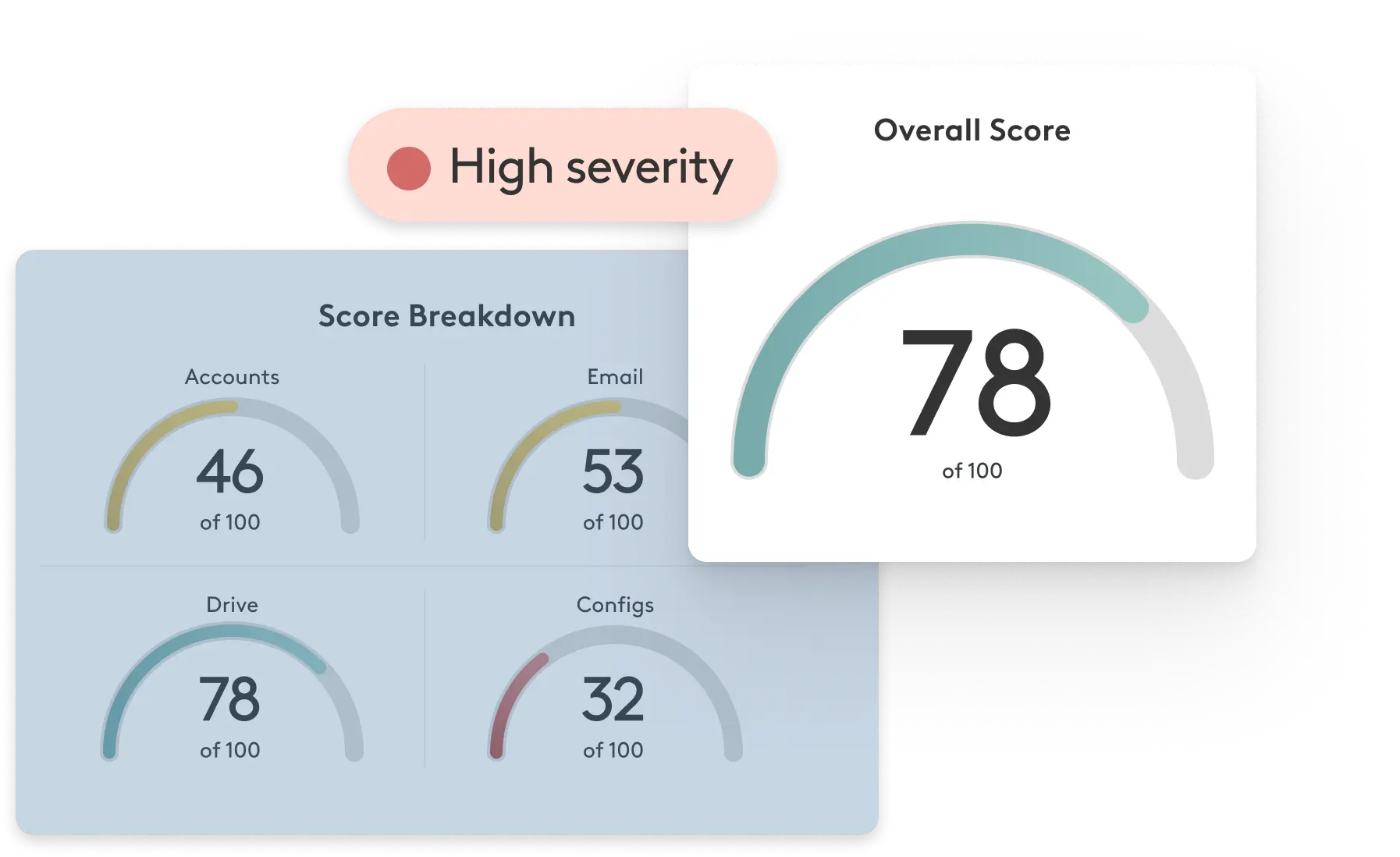
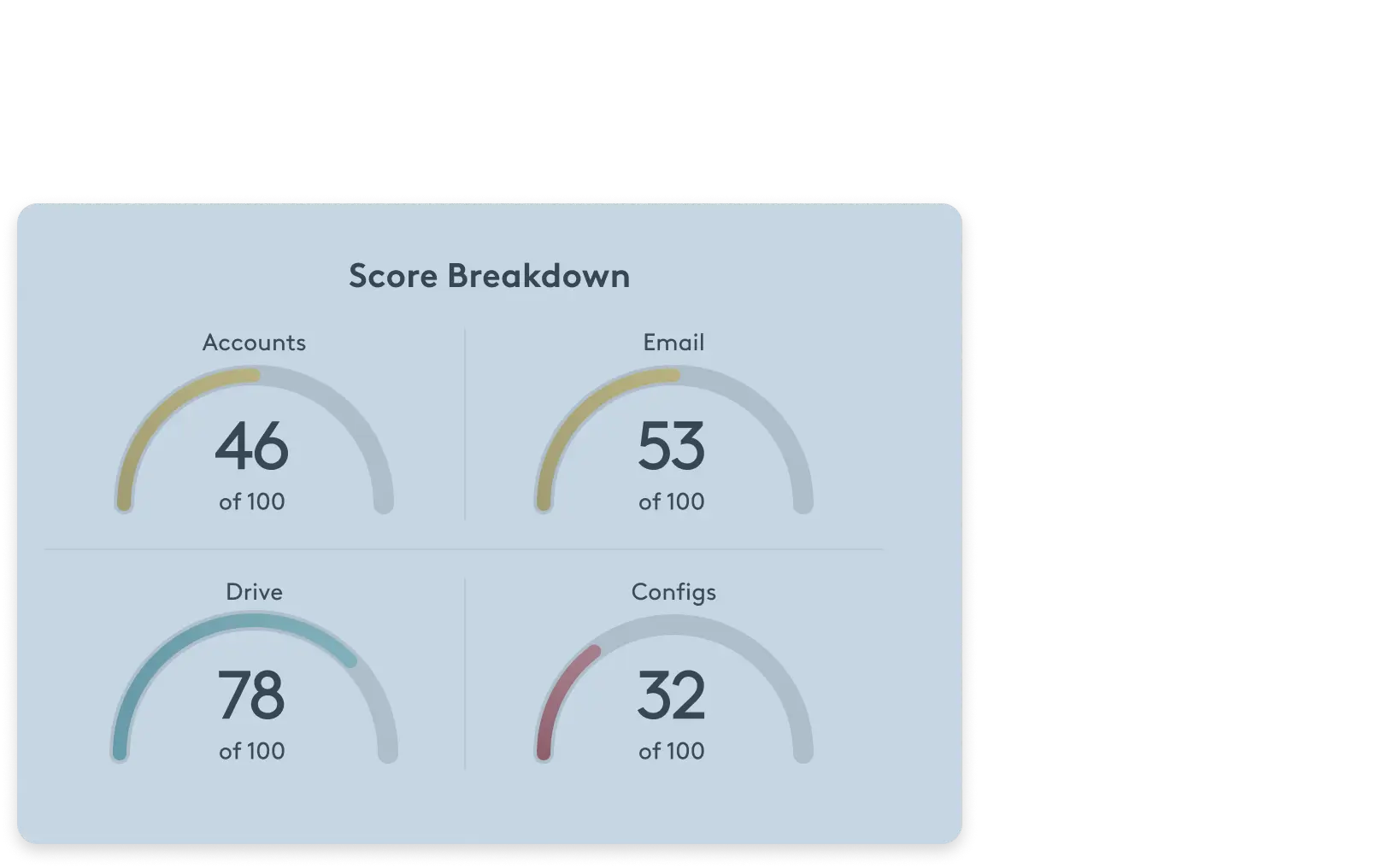
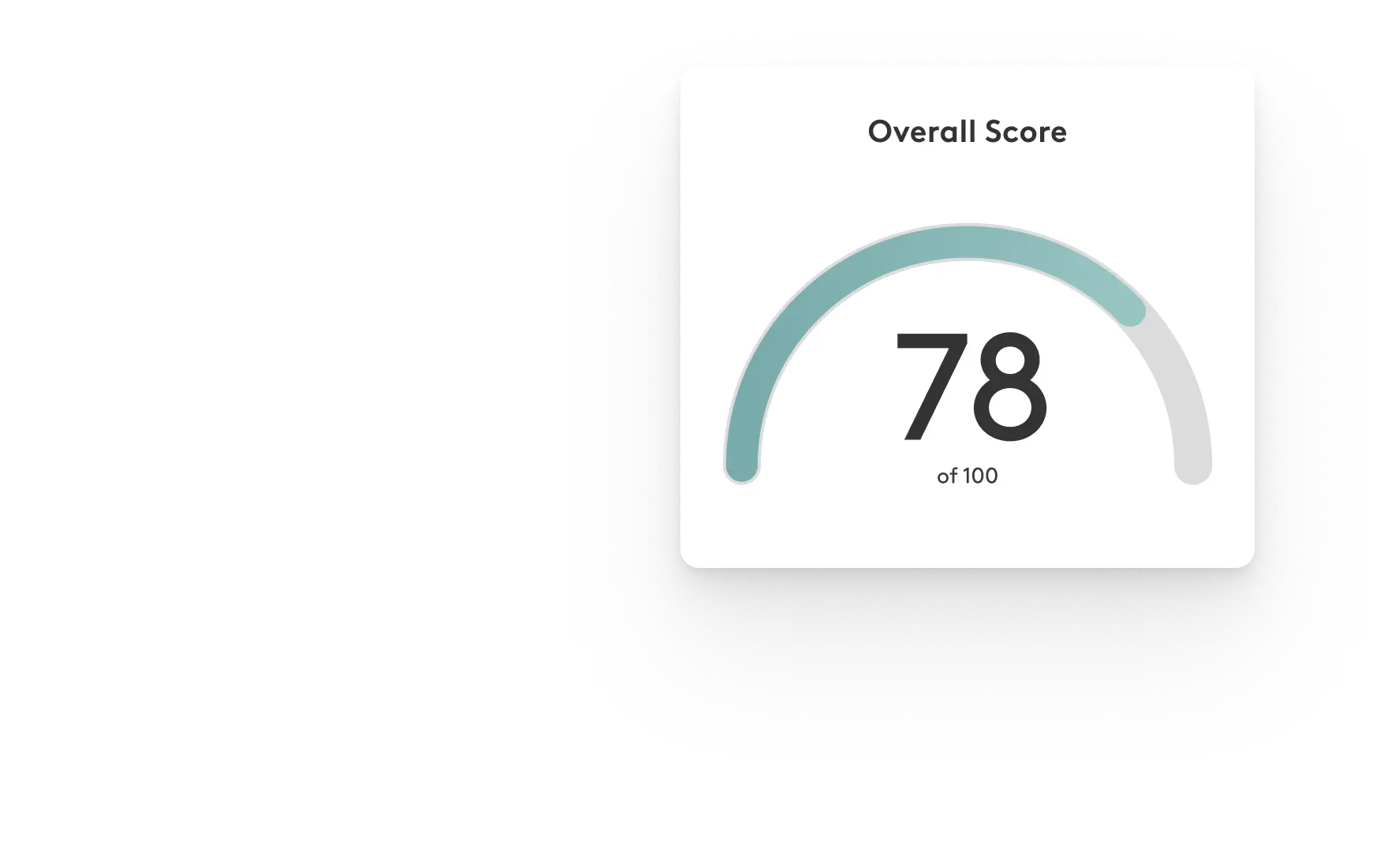
Check your Workspace security posture now
Material’s scorecard evaluates your approach to email, file, and account security, providing actionable recommendations to improve your security today. Stop guessing and evaluate now.