Our Customers
-svg.svg)

%20(1)-svg.svg)
.svg)
-svg.svg)


-svg%20(1).svg)





%20(2).avif)

.svg)






How top security teams use Material
.png)


"The 'aha moment' came when we realized Material Security wasn’t just a technical product, but a cultural one. By design it reinforces good security culture and collaboration."
.avif)


“If we review the last 5 years of incidents across multiple industries, both sophisticated and wide-spread attacks started with a successful intrusion through phishing. Material gives us an extra layer of protection when it matters most—and accelerates our detection and response time by delivering a strong workflow.”



“I think it’s important to look at the cloud office at a wider holistic level and not just at the point of entry. Understanding its whole life cycle and even what’s being done with it when resting is critical to protecting that platform. Material does that very well.”
.png)


“I've seen amazing improvements in our ability to react, relying on well-trusted mechanisms from Material. With just one click, we can disable phishing emails.”
.png)


"We knew critical aspects of Google's Workspace native security wouldn't scale as our company got bigger, which is why we came to Material.”


.webp)
“The plan was to find something more holistic for email security. We always consider how to best maintain security and privacy while improving usability.”



“The Material team is highly engaged. They're in our real time communication channels with us. They go above and beyond in terms of delivery. And we see that time and time again. I mean, I can't say enough good things about them.”
.jpeg)


“We're seeing much better adoption because Material allows us to tailor our phishing campaigns to what we're actually seeing in the industry. And it takes a lot of that burden off the end user, which is fantastic for us.“
.png)


“With Material, we have a mightier team because automation takes away the toil. The security team doesn’t need to check every email and do all the data mapping across multiple tools. It’s so much easier.”

SafeBase extends protection across Google Workspace and makes security operations proactive
.png)


“One of the big things that makes Material unique in this space is their team, which is professional to an extraordinary degree.”


.avif)
“When it comes to filtering phishing attempts, Google is a good start. But as a fintech company that handles sensitive data, we wanted a more robust tool. With Material, Carta has increased its phishing awareness posture.”
.jpeg)


"The best thing about the phishing features in Material Security is I haven't had to do anything like a phishing campaign. I've loved the interactivity of it all.”
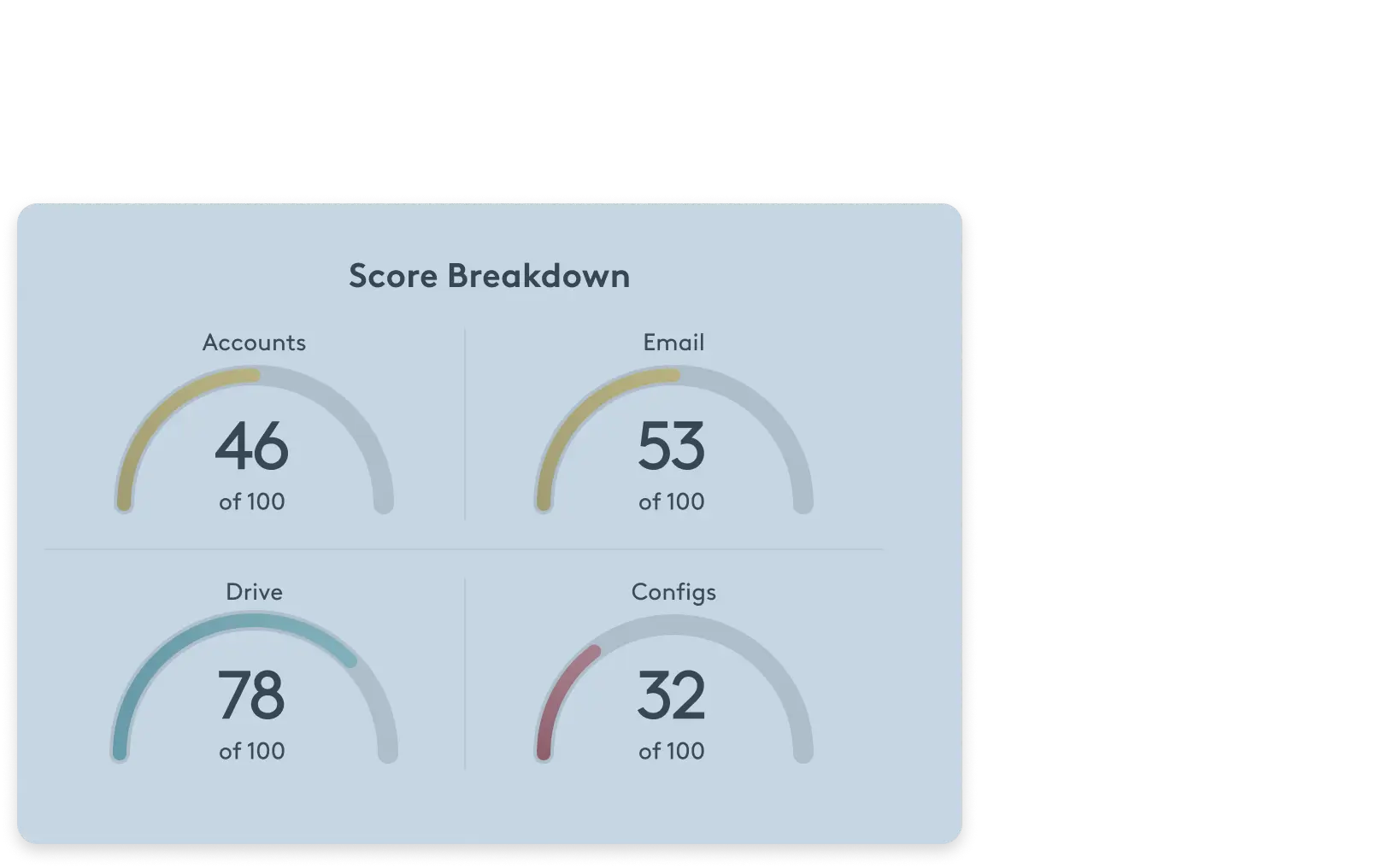
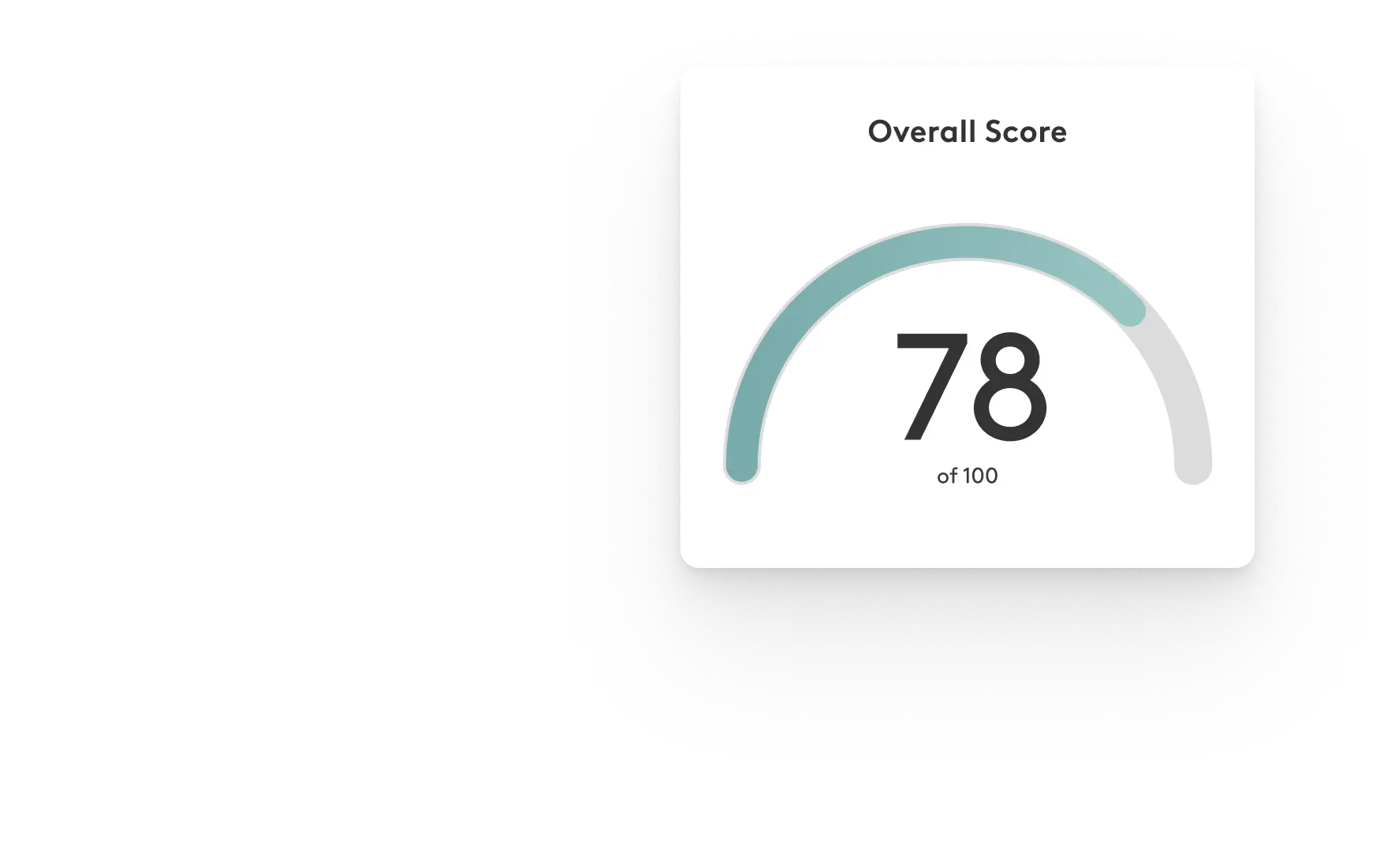
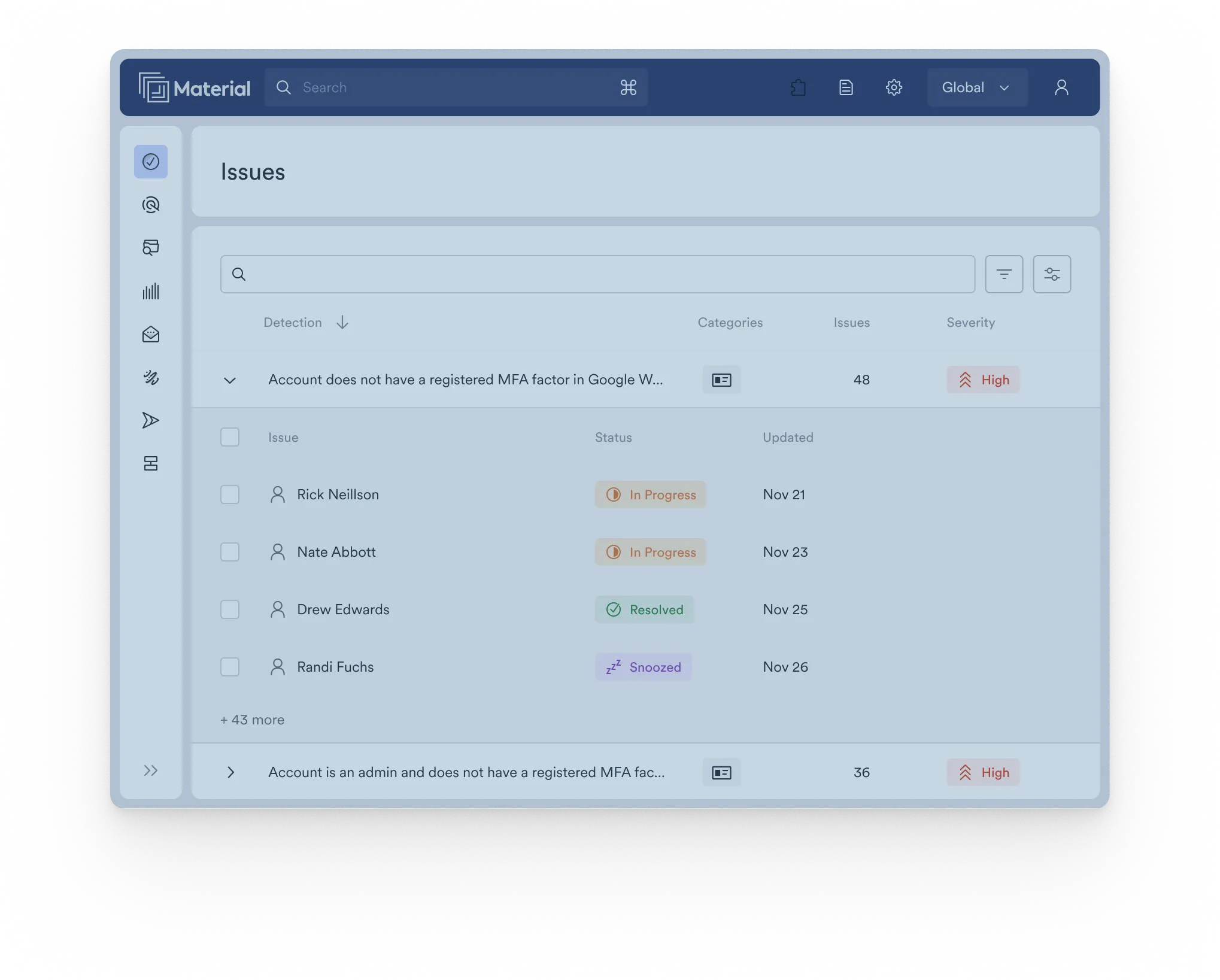
Check your Workspace security posture now
Material’s scorecard evaluates your approach to email, file, and account security, providing actionable recommendations to improve your security today. Stop guessing and evaluate now.
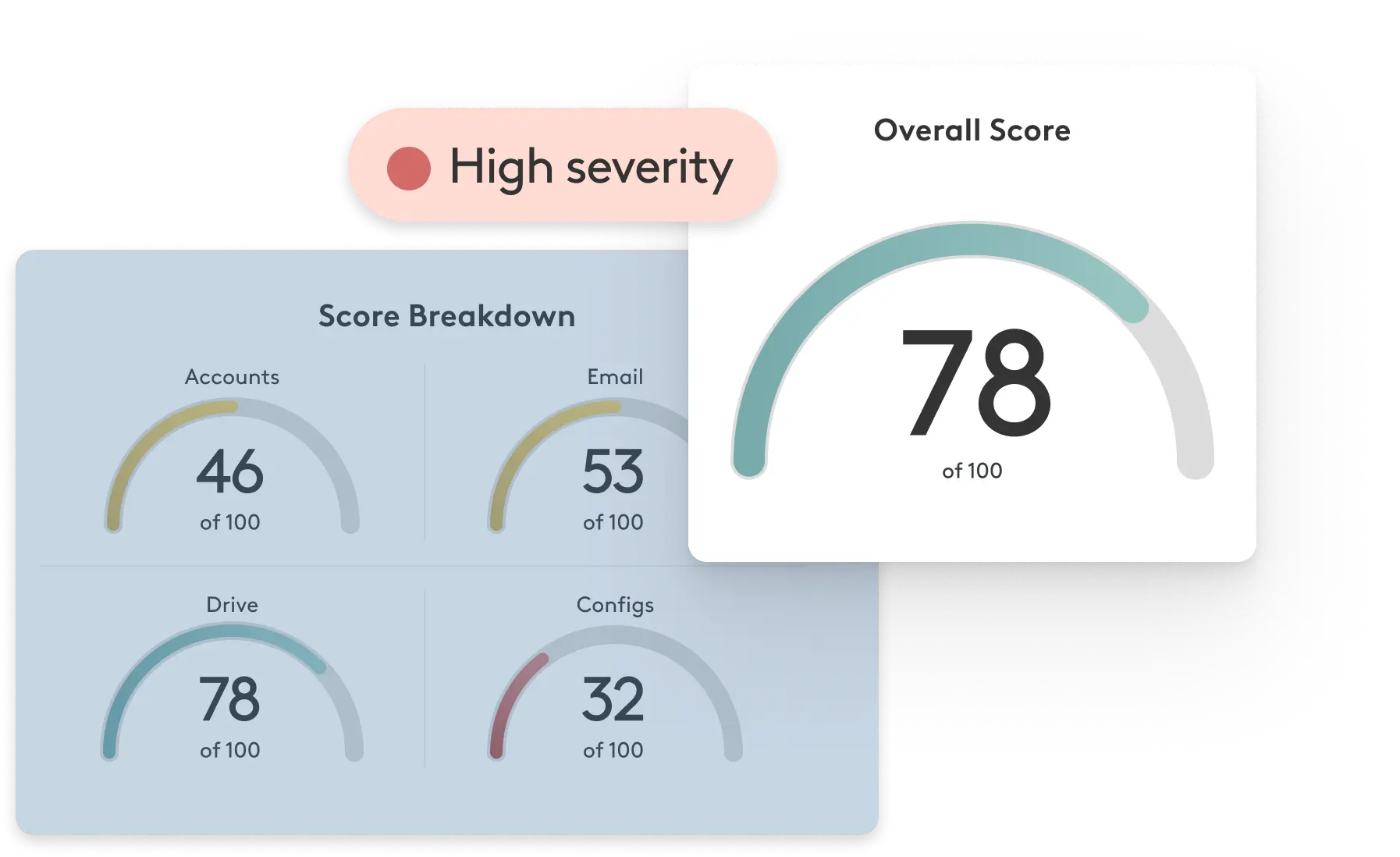

.png)



.png)
.png)

.avif)


.avif)



%20(1).avif)

.avif)


.avif)
.avif)



%20(1).avif)
.avif)
-svg.svg)
%2520(1)%2520(1).avif)

.avif)

.avif)