Material elevates Account Takeover (ATO) detection beyond basic IP logging by integrating real-time network intelligence from Spur, instantly differentiating legitimate remote work from sophisticated proxy-based attacks.
On its own, an IP address is effectively a random string of numbers, not a security signal. In a world defined by hybrid work, corporate VPNs, and global contractors, that IP address alone tells you very little. Is it a legitimate remote connection, or is it an attacker hiding behind a disposable proxy?
Without any additional context, every ambiguous login becomes a triage headache—a suspected Account Takeover (ATO) that often turns out to be nothing more than a user working from a coffee shop with a poor VPN configuration.
Ambiguity doesn’t scale in security. It leads to alert fatigue, missed signals, and wasted analyst time. We built Material to remove that ambiguity. That’s why we’ve incorporated advanced network intelligence directly into our cloud workspace activity logging and threat detection pipeline.
The Blind Spot of Native Cloud Workspace Logging
The native logging within cloud platforms like Google Workspace is fundamental. It tells you who and when, but it routinely fails to answer the critical security question: what kind of network is this?
For security practitioners, this lack of context presents two major challenges that directly contribute to the friction of ATO detection:
- Noise from Legitimate Flexibility: Remote and hybrid work is the norm. Users connect from home, from co-working spaces, and sometimes (dare we say it?) from commercial VPNs. When a user logs in from an IP that has never been seen before, the native platform flags it as anomalous. Your analyst now has to chase down the user, creating a friction point that slows down incident response and makes security a drag on productivity.
- Silence from Subtle Attacks: Attackers know to avoid obvious Tor exit nodes—sometimes. But a sophisticated ATO often comes through a residential proxy or a bulletproof hosting network. These networks are designed to evade standard blocking checks by appearing to be legitimate consumer infrastructure. To a raw log, an attacker using a rented residential IP looks just like a remote employee working from their home internet. The native platform often misses this entirely, leading to a silent compromise.
We can’t solve the complexity of modern network infrastructure by asking our teams to manually cross-reference every suspicious IP with multiple external threat feeds. Particularly in the context of IPv6 proxies and the faster rotation of IP addresses they allow, the detection must be smarter than the log itself.
Enriching the Signal: From Ambiguity to Action
Material's approach integrates a continuous feed of IP intelligence–in particular Spur–enriching every single cloud workspace activity log with deep, real-time network context. Spur's IP enrichment provides high-fidelity intelligence that classifies incoming traffic, revealing if a login attempt originates from an anonymization service like a VPN, residential proxy, or bot network. With the intelligence provided by Spur, we’re able to turn a generic IP address into a rich data object that answers the "what kind of network" question immediately.
Here’s the shift: instead of just a raw IP, your login event now includes crucial attributes about the connection's origin.
Network Context Signals: Understanding the Infrastructure
These signals help your team quickly understand the nature of the network being used, making the distinction between benign remote work and malicious infrastructure immediately apparent:
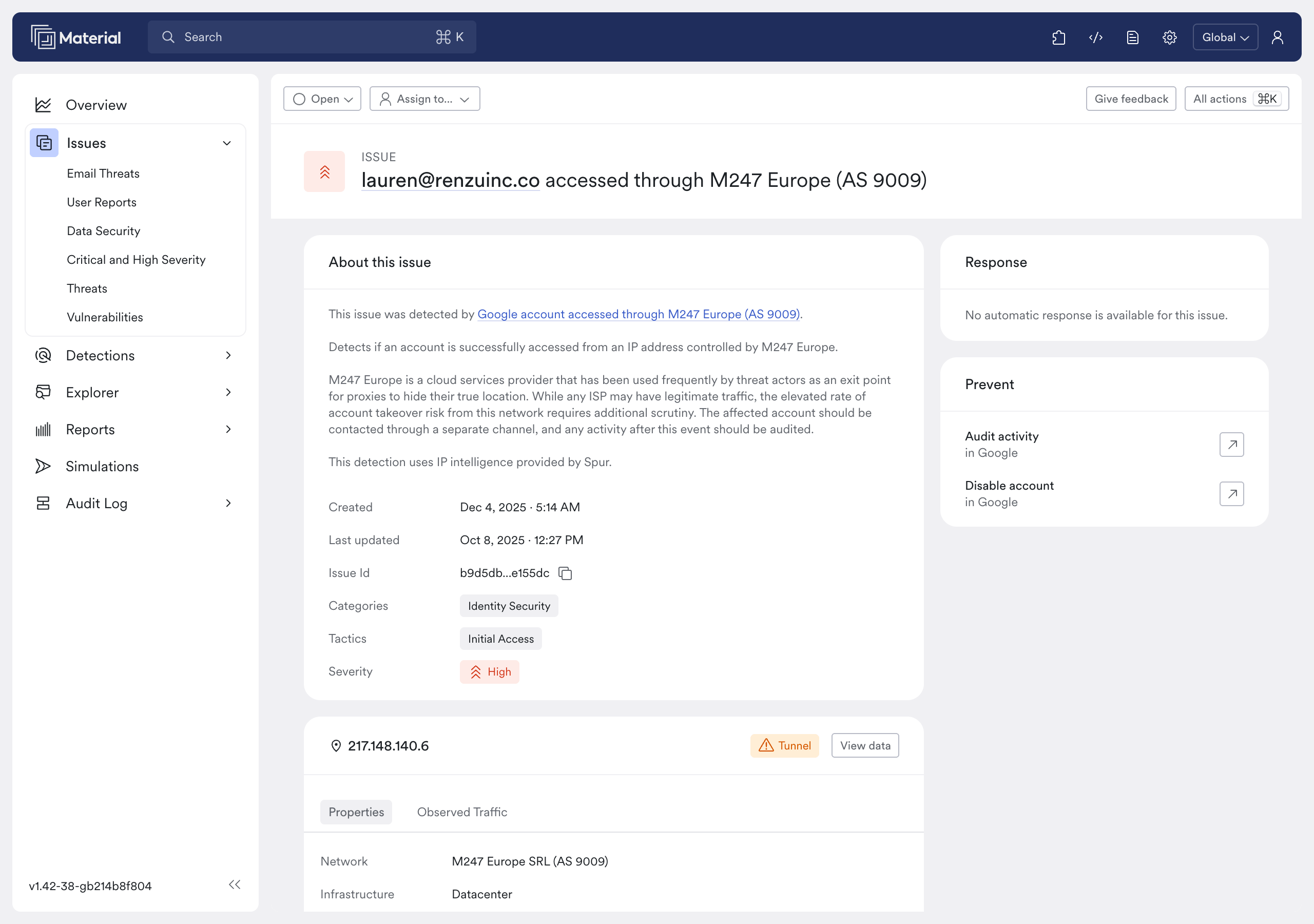
- Proxy/VPN status and provider: Is this connection routing through a known anonymizing VPN, a commercial proxy service, or a Tor exit node? We gain explicit insight into the infrastructure type. A login from a Tor exit node, while rare, is an immediate high-risk finding. A login from an Astrill VPN is highly suspicious, while a connection from a known corporate ZTNA gateway can be immediately dismissed.
- Hosting Provider Identification: We can identify if the connection originates from a major datacenter or cloud hosting provider (e.g., AWS, GCP). While this isn’t malicious on its own, a normal employee login from a data center IP is highly irregular and warrants immediate review.
- Sanctioned Geolocation: Instantly flag connections originating from countries sanctioned by bodies like OFAC. This provides a clear, policy-driven detection signal for regulated environments.
Threat and Risk Signals: Identifying Malicious Intent
Beyond just classifying the infrastructure, we layer in dynamic threat intelligence based on observable behavior:
- Observed Malicious Behavior: Flag connections that have been recently associated with known malicious activity, such as recent brute force attacks against web forms or headless web scraping activity. These are networks where bad actors are actively operating.
- Residential/Malware Proxies: This is a crucial differentiator. These are IPs that attackers rent to look legitimate. By identifying them explicitly, we can flag a genuine threat that native anomaly detection would likely ignore.
This is the pragmatic reality: an IP address is only as useful as the context you overlay onto it. Material does this for you automatically, augmenting the native Google Workspace logs that often leave practitioners working with half-formed clues.
Immediate, Actionable ATO Detection
For the security practitioner, the impact of this enrichment is felt in two key areas of the ATO detection and response workflow:
1. Simple, High-Fidelity Detections
We can now build simple, high-confidence detection rules based on explicit intelligence, reducing the risk of false positives that plague geo-based or time-based anomaly rules. For example, Material enables the security team to set a clear policy to automatically quarantine a session or block access immediately if a successful login originates from a Tor exit node or a network with a confirmed history of recent brute-force attacks.
2. Enhanced Triage and Investigation
When an alert does fire, your analyst doesn't have to leave the Material platform to begin the investigation. The enriched context is right there in the event log.
- Clear Triage: Instead of seeing an IP from "Seattle" and wondering if it's the user's home or a shady proxy, the analyst sees "Seattle, WA - Residential Proxy/High Risk." The ambiguous signal is instantly resolved into a clear, actionable finding.
- Faster Remediation: By classifying the type of threat, your team knows immediately what response is required—a session termination for a high-risk proxy login, versus a simple user check-in for a legitimate but irregular remote connection.
Confident Detection in a Complex World
This is just the start. By incorporating deep network intelligence at the login layer, we lay the groundwork for building far more nuanced behavioral analytics across the entire cloud workspace.
Security isn't about collecting the most data; it's about giving your team the most actionable context. By integrating network intelligence directly into your cloud workspace activity, we're cutting through the noise to deliver confident, high-fidelity ATO detection that works where the native tools fall short. It's security that reflects the pragmatic, complex reality of how people actually work.

.png)
.png)



