November 06, 2023 · 5m read
Join us for a live ask me anything (AMA) session on January 25th around this topic. RSVP and submit your questions here.
The Securities and Exchange Commission (SEC) recently announced new regulations that go into effect on December 18, 2023, requiring public companies to disclose cybersecurity incidents deemed material, and to disclose on an annual basis material information regarding their cybersecurity risk management, strategy, and governance. The open question is – who decides what is “material”, and are security incidents securities fraud? I’ll leave the latter question to Matt Levine, but for security incidents, let it be known if it wasn’t already – the SEC is watching.
The SEC? They have boats? (Note: I have a self-imposed limit of one Arrested Development reference per blog post. That’s my one.)
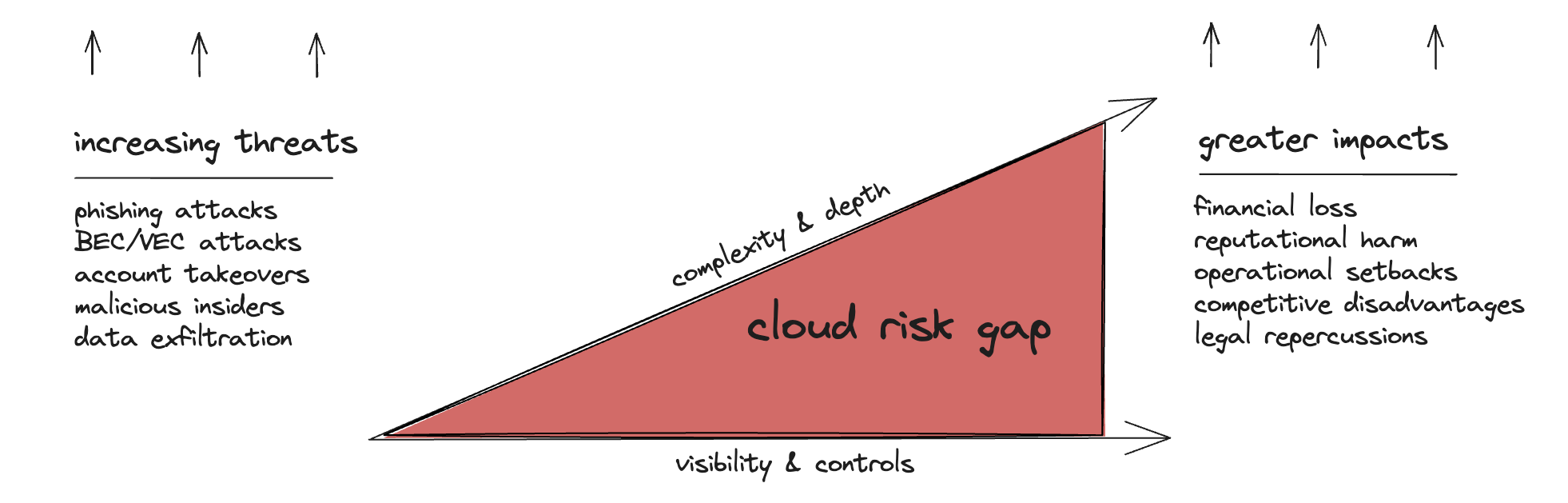
The Cloud Risk Gap
Security and risk teams are grappling with an expanding cloud risk gap. Amidst increasing threats that have greater material impacts, the complexity & depth of a typical cloud environment is outpacing the security & operational controls to support it – further widening the risk profile to contend with. The gap isn’t limited to technology – as teams are being asked to do more with less given macroeconomic conditions, the challenges with people and processes further compound the issue.
Risk assessment is hard to measure. There’s enough compliance guidelines to provide an endless task list, but as every great security practitioner knows, compliance does not equal security. While more preventative measures are always a good thing, the reality is that efforts are still largely reactive.
The definition of "material impact" might be subject to interpretation, but the consequences are unequivocal – they lead to financial loss, reputational harm, operational setbacks, competitive disadvantages, and legal repercussions. While the SEC is the authority that may impose fines or bring charges in extreme cases, it's the erosion of investor confidence that each material impact causes which truly shakes the foundation of a company.
The practice of promptly and responsibly disclosing security incidents is hardly a new phenomenon, but what sets this particular framework apart is the obligation to report not just the incident itself, but also to provide a detailed account of the breach's financial impact, blast radius, and incident response efforts. In that sense, these guidelines aren’t just another checklist; they represent an enforcement of good security posture and practices. Who would have guessed? In the most positive framing – this isn’t just compliance box-ticking, it's an actionable playbook for resilience.
In practical terms, what companies are required to do when they disclose a security incident is to file an 8-K form within 4 days of determining that an incident is material. The contents of an 8-K form include:
- A clear and detailed account of the incident, including a timeline of events.
- Identification of the systems, networks, and accounts that were affected.
- The nature and scope of the sensitive and regulated data that was compromised.
- An assessment of the operational impacts stemming from the incident.
- A comprehensive description of the response to the incident, including immediate actions taken.
- A strategy or plan for mitigating the risks to impacted systems and preventing future occurrences.
- Any information that investors would deem important related to the incident.
An important condition of these guidelines is that the form is to be submitted within 4 days of the incident being determined as material, not 4 days after the incident is discovered – another element open to partial interpretation, although the guideline does specify, “without unreasonable delay”. As public companies are subject to public market forces, the timing of a disclosure is as important as its contents.
Avoid material impacts. Gain Material Security.
The obvious thing to recommend with these regulations would be for security & risk teams to establish controls and procedures to properly assess and respond to a security incident – saying that is the easy part. But amidst the growing cloud risk gap, the hard parts are defending against increasingly sophisticated attacks, understanding the growing sprawl of sensitive and regulated data, and adhering to a larger number of company security policies. What makes these hard parts so hard is that incident response processes are still largely manual, security teams lack central visibility to stay ahead of misconfigurations and vulnerabilities, and there’s far too much data to even classify, let alone control.
There is no silver bullet in security, and there never will be. Pun aside, at Material Security, we aim to reduce the risk profile of the cloud office – Microsoft 365 and Google Workspace – by acting as a force multiplier in otherwise hard to address, critical areas.
Focusing on the fundamental aspects of cloud office security—email protection and data loss prevention—the traditional methods fall short. Typically, security would rely on a gateway to filter incoming and outgoing traffic, aiming to block threats and secure sensitive information. This method is far from foolproof, often riddled with false positives and negatives—you can’t close the risk gap with a fly swatter.
One core issue is that the gateway architecture isn’t suited for the dynamic cloud operating model. Moreover, the traditional siloed approach to threat detection fails to consider the full threat lifecycle – handling both incoming threats and outgoing exfiltration requires a level of inspection within the provider itself to be effective. At Material, we adopt a holistic stance on cloud office security. With intelligent threat defenses and right-sized access controls, we synchronize the protection measures with the actual flow of communications and data, addressing security in real time and across the entire workspace.
For the important use cases of handling sophisticated email-based attacks and blocking regulated data exposure, Material offers Phishing Protection and Data Protection. In a full threat lifecycle scenario, you want a solution where the active defenses surface issues that deserve to be triaged with the right context to remediate, and in the cases when an attack gets through or an insider goes rogue, the compromised account is prevented from accessing sensitive contents.
Accelerated incident response workflows plus minimized likelihood and impact of a breach: there’s the force multiplier.
Start With Heightened Posture
It’s important to remember that your productivity suite – Microsoft 365 or Google Workspace – isn’t just another application, it’s critical infrastructure. The surface area is a lot to contend with – along with strong defenses and controls, visibility into risky behaviors and settings is an important aspect to risk mitigation.
Also acting as a force multiplier in otherwise hard to address, critical areas, Material Posture Management is a simple way to gain instant insights into high risk behaviors and settings such as MFA adoption and possible bypasses, email forwarding, classified contents in mailboxes, partner access, 3rd party app usage, and more.
It’s quick to see for yourself – Material connects to Microsoft 365 and Google Workspace via API in minutes, and once accounts are enrolled, immediately begins building a structured data model of your people, content, and communications over time. As one customer so succinctly put it – “at that point it wasn’t a Proof of Concept, it was Proof of Value.”
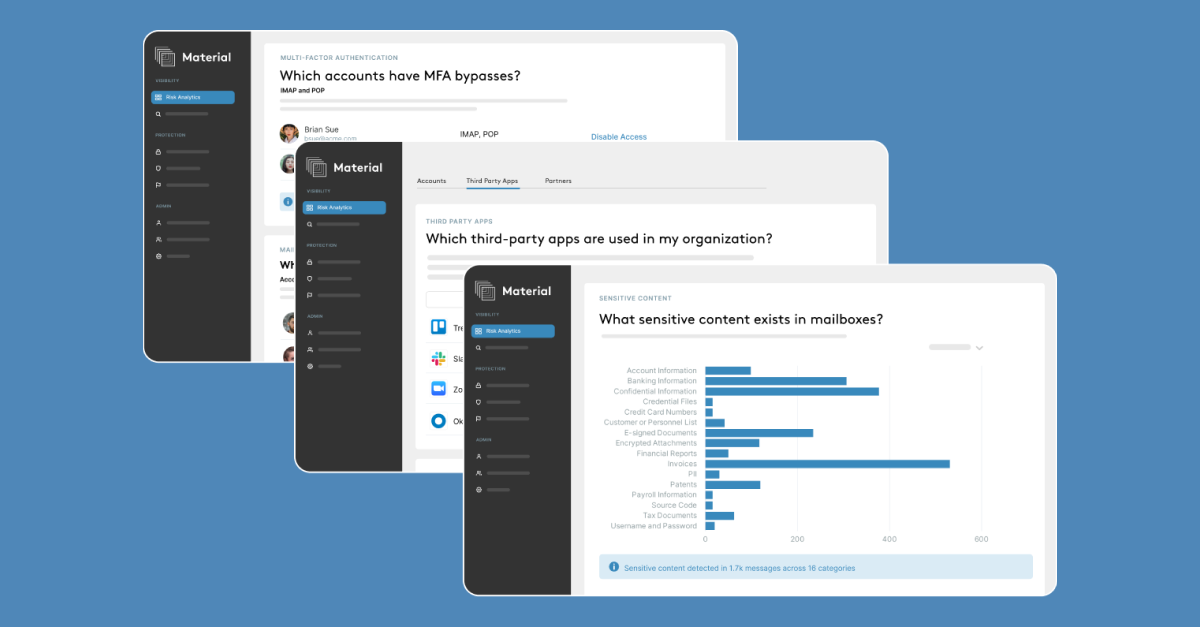
Get in touch with us to see your cloud office risk profile for yourself ->
Still have questions on the impact to you and your business? Join our ask me anything (AMA) session on January 25th: RSVP and submit your questions here.

