A guest post by Shasheen Bandodkar to explore why MFA falls short against sophisticated BEC attacks in Google Workspace and learn resilient defense strategies to protect your organization.
Introduction
Business Email Compromise (BEC) is more than a security incident; it's a direct threat to a company's financial stability and operational integrity. And for organizations that rely on cloud workspaces like Google Workspace, these sophisticated fraud attacks almost always begin with a single, successful account takeover (ATO). A single compromised account is all an attacker needs to impersonate a trusted colleague and orchestrate a devastating financial loss or data breach.
The reality is stark. While multi-factor authentication (MFA) was once considered the gold standard for account protection, it is no longer failsafe when relying on it purely for initial access. This post will examine why a defense strategy focused only on preventing the initial login is insufficient for Google Workspace environments. A modern defense must also focus on reducing the blast radius of a successful compromise and preparing for rapid recovery, neutralizing the threat before a fraudulent wire transfer ever leaves the bank.
The evolution of the modern BEC attack
The anatomy of a BEC attack has evolved from simple password guessing to a patient, multi-stage operation. Attackers have become adept at bypassing traditional security controls and, most importantly, blending in with normal user behavior to remain undetected.
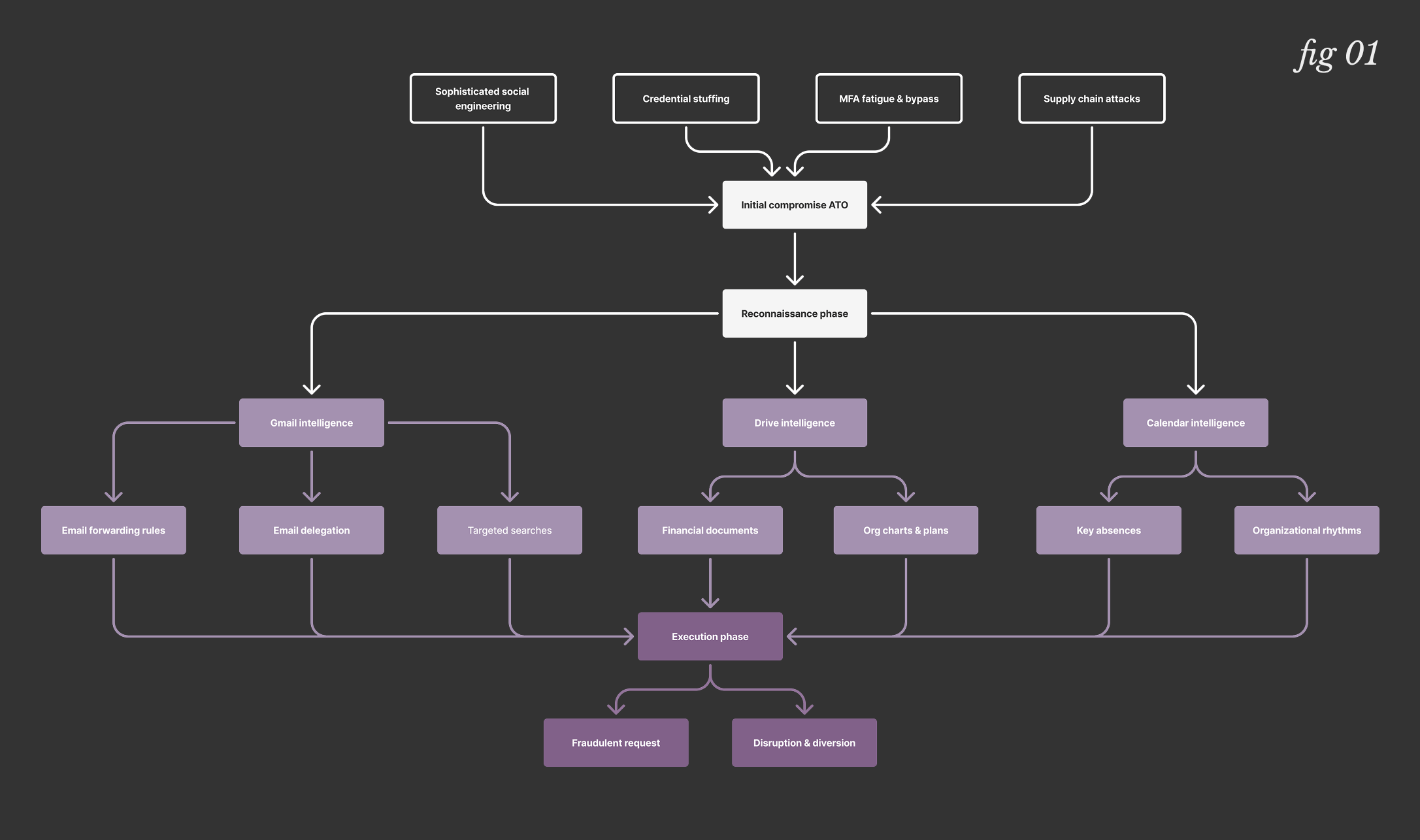
The initial compromise—the ATO—often relies on a few key methodologies:
- Sophisticated Social Engineering: Phishing has moved beyond clumsy, typo-ridden emails. Modern campaigns are highly targeted and psychologically manipulative.
- Credential Stuffing: With billions of stolen credentials available on the dark web, attackers systematically test them against corporate accounts, exploiting our tendency to reuse passwords.
- MFA Fatigue & Bypass: Attackers now use everything from SIM swapping to prompt-bombing (spamming a user with MFA pushes until they relent) and stealing session cookies to sidestep authentication controls.
- Supply Chain Attacks: Targeting trusted third-party applications with OAuth access to your Google Workspace environment provides a persistent, and often unmonitored, foothold.
Why Google Workspace is the perfect platform for BEC
For an attacker planning a BEC campaign, Google Workspace isn't just a target; it's the ideal operating environment.
- A Platform of Trust: An email from a colleague's real account is inherently more believable than one from a suspicious external address. The entire attack leverages your organization's own infrastructure against itself.
- A Centralized Treasure Trove: An inbox contains a rich history of communications, contracts, and internal procedures. Attackers don't just guess how to craft a fraudulent request; they study past conversations to mimic tone, timing, and terminology perfectly.
- Integrated Scaffolding: Access to one account often provides access to everything else—Drive, Calendar, Contacts—which can be used for reconnaissance to make the eventual BEC attempt more convincing.
- Disruption as a Diversion: An attacker can cause operational chaos to distract security teams while the real financial fraud is taking place.
The false sense of security from legacy controls
When leadership hears "we have MFA," there's often an unearned sigh of relief. This overconfidence in a single preventative control is exactly what attackers exploit. It leads to critical gaps:
- Reduced vigilance and a belief that the account access problem is "solved."
- Inadequate monitoring of post-authentication activity. The focus remains on the front door, not what happens once someone is inside.
- Deficient incident response plans that are not equipped to handle an attacker who appears to be a legitimate, authenticated user.
Common attack patterns for BEC in Google Workspace
An attacker with account access will use a combination of tactics to prepare for and execute a BEC attack. The goal is to gather intelligence and manipulate communications without being detected.
Gmail: The BEC launchpad
The inbox is the central hub for reconnaissance and execution.
- Email Forwarding and Filtering: The first thing an attacker often does is set up forwarding rules. They can silently copy all incoming mail to an external address to study communication patterns. They also create filters to automatically delete replies to their fraudulent emails from the "Sent" folder, preventing the real user from discovering the conversation.
- Email Delegation: Granting a personal Gmail account delegate access is a simple way for an attacker to maintain a persistent foothold in the inbox, even if the user's password is changed.
- Targeted Searches: Attackers will search a compromised mailbox for keywords like "invoice," "payment," "wire transfer," or "contract" to identify financial processes and key personnel.
For example, Google Workspace Audit Logs might show, 'User cfo@company.com created mail filter rule forwarding all emails containing "invoice" to external address competitor-intel@tempmail.com at 2:47 AM from IP address in Nigeria 3 hours after successful MFA authentication from company headquarters.' This pattern of post-authentication rule creation from anomalous locations is a classic BEC precursor that traditional perimeter security would miss.
Google Drive: The reconnaissance goldmine
The corporate file cabinet is where attackers find the templates for convincing fraud.
- Exfiltrating Financial Documents: Attackers look for past invoices, wire transfer forms, and vendor contracts. This allows them to create fraudulent documents that are indistinguishable from legitimate ones.
- Data Mining for Social Engineering: Employee lists, org charts, and project plans found in Drive help attackers understand internal relationships and power structures.
Google Calendar: The playbook for timing the attack
The calendar is a surprisingly valuable source of operational intelligence.
- Identifying Key Absences: An attacker can check the CFO's calendar to see when they are on vacation. They then send an "urgent" wire transfer request to the finance team, knowing the CFO is unavailable to verify it.
- Mapping Organizational Rhythms: Understanding when board meetings or financial reporting periods occur allows an attacker to time their request for maximum impact and minimal scrutiny.
OAuth Applications: The Persistent Backdoor
Third-party applications with OAuth access to Google Workspace represent a particularly insidious attack vector because they survive password resets and often escape routine security audits. An attacker can compromise a legitimate business application (like a CRM or project management tool) or create a convincing fake app that requests broad Gmail and Drive permissions.
Once authorized, these applications can silently access emails, download files, and monitor communications indefinitely—even after the initial compromise is discovered and remediated. Unlike direct account access, OAuth tokens don't trigger standard login alerts, making this persistence mechanism nearly invisible to traditional monitoring.
Building a Resilient Defense Strategy
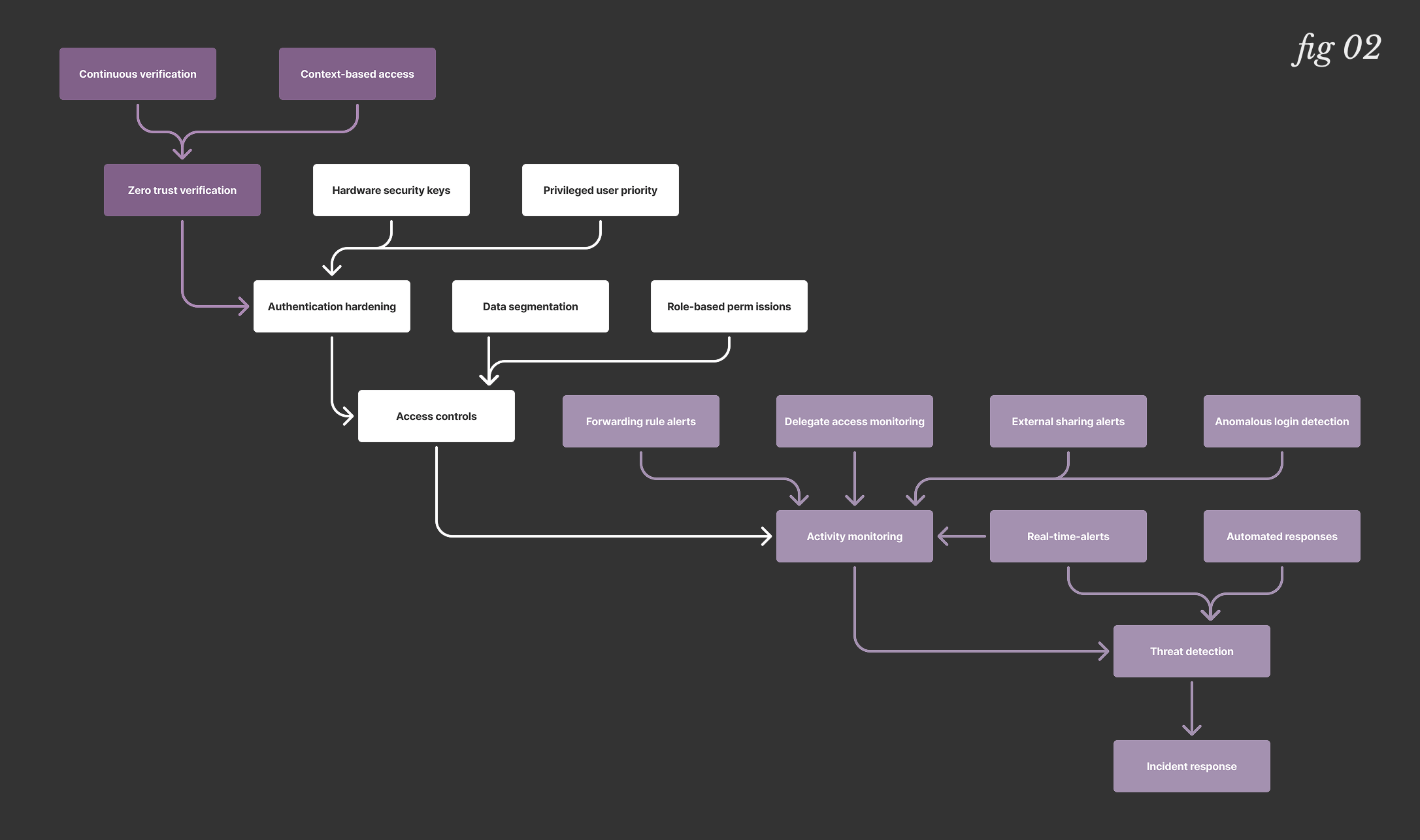
Proactive resilience is the best protection. A defense-in-depth strategy for Google Workspace must assume that a compromise will eventually happen and focus on limiting the damage.
- Start with Zero Trust principles. Move beyond one-time authentication. Every request should be continuously verified based on context like user behavior, device health, and location.
- Harden your authentication. Phishing-resistant hardware security keys (FIDO2) are the strongest defense against credential theft. Prioritize rolling them out to privileged users and executives first.
- Implement least privilege. A user in marketing shouldn't have access to finance folders in Google Drive. By segmenting data access, you starve an attacker of the reconnaissance materials they need for a convincing BEC attack.
- Monitor post-authentication activity. Your security tools should be able to detect and alert on the precursors to a BEC attack, such as:
- A new, suspicious email forwarding rule.
- Anomalous delegate access being granted.
- Unusual external sharing of sensitive files from Drive.
- A user logging in from a new location and immediately searching for "wire transfer."
Without preparation, the incident response to a potential attack becomes significantly more difficult. When finance calls to verify an 'urgent' wire transfer request, you've already moved well beyond prevention: you’re in damage control mode. Once you have initial signs of a BEC attack, immediate containment becomes critical: reset credentials, revoke sessions, audit forwarding rules, and review file shares created in the past 30 days. Perhaps most importantly, assume the attacker has studied your communication patterns and adjust verification procedures accordingly.
As the old cliche goes, an ounce of prevention is worth a pound of cure. Hardening your environment and building a resilient defense-in-depth strategy to BEC attacks is time well spent–you’ll thank yourself later.
Conclusion
Focusing exclusively on preventing account takeovers is like locking the front door but leaving all the internal doors wide open. The true risk to the business isn't the ATO itself, but the BEC attack and other downstream chaos it enables.
A resilient security posture is one that embraces a layered approach. It hardens the perimeter, but it also relentlessly monitors the environment for the subtle signs of an internal threat. It moves beyond simple user awareness training to implement technical controls that can detect an attacker who is patiently reading emails and preparing to strike.
By viewing security through the lens of business risk—and understanding the specific tactics used to turn a compromised account into a fraudulent transaction—organizations can build a Google Workspace environment that is resilient by design.
This is a guest blog post from Shasheen Bandodkar, a security architect and researcher specializing in cloud security, offensive security, and vulnerability management.

.png)
.png)
.jpg)

